Leaderboard
Popular Content
Showing content with the highest reputation since 07/13/2024 in Posts
-
9 points
-
[ Introduction ] Hi @everyone, in recent times, Android has just released version 14, which includes some SDK restrictions. The requirements are that apps should at least be under SDK version 24+, or else installation fails. Another problem is that Game Guardian hasn't been updated for years (March 22, 2021, since the last update), a total of 2 years. I understand that life can be unbothered sometimes, and I hope there's some confirmation regarding this instead of intending it as an "unforseeable future" kind of thing. I've seen a rising number of these issues on Help, General Discussion, and in other possible sections of the forum. I recommend anyone who has a newer device or just recently updated to Android 14 to follow this topic. Here, I propose several possible solutions regarding this issue: [ Main Course ] You can bypass SDK enforcement using shell commands, which you need to install Game Guardian manually through command line. You can achieve this through ADB: Android Debug Bridge or Termux: Terminal for Command Line application. This tutorial will split into 2: { ADB: Android Debug Bridge } This step doesn't require "Root" permission, but before proceeding into the main tutorial. We should prepare several things: Computer / Laptop running Windows OS A cable data Download ADB depedencies: here Android device with "USB debugging". If your device "cant be recognized" or simply not exist on "Device Manager", you need to install: Universal ADB Driver Then read: XDA: Install ADB & Enable USB Debugging. Now put this command on your command prompt / powershell / gitbash / or whatever terminal you use: # Check if our device works properly adb devices # Install Game Guardian manually through ADB adb install --bypass-low-target-sdk-block <path_to_game-guardian.apk> # If ADB is unresponsive / bugged, do: adb kill-server adb start-server { Termux: Terminal } The only requirement is you need "Root" permission, this is the most easiest way. Since you're going to Install Game Guardian, I assume you already have one (Yes, Game Guardian requires "Root" permission, duh). Download: Termux and Just go ahead execute this command: pkg update pkg upgrade pkg install tsu pkg install android-tools sudo adb install --bypass-low-target-sdk-block <path_to_game-guardian.apk> { Virtual Machine } This is suitable way for non-rooted users. Android 14 is relatively new, some of your ROM/OS might not support "Rooting" yet. Virtual Machine allows you to emulate another Android inside your Android 14 (or etc). Usually it comes with older Android version. I suggest to use Virtual Machine with Android 7 or 9 as you're not going to face any redundant issues, like Android 10-14 did. I would recommend using "VPhoneGaGa": VPhoneGaGa VMos Pro X8Sandbox F1VM { Modded APK } You can try to edit Game Guardian SDK: ("android:targetSdkVersion" to version 24+) and ("android:minSdkVersion" to 24+) on Manifest.xml using: APK Editor. You can also download already modded Game Guardian here (credit to @HEROGAMEOfficial ) : : Game Guardian : [ Aftermath ] With that, you can simply reference this topic in case there's someone that facing the same problem. I hope this topic can help you and other people. Thank you for reading.8 points
-
Possibly... This game able to be dumped? The free one used to: https://animalcrossing.fandom.com/wiki/Animal_Crossing_Wiki:Data_Extraction_Project/PC It would make finding/adding content easier. As for the currency, I'll try to come up with a user friendly guide.7 points
-
View File Online Mega Script v04 (100% Free & Not Encrypted) New Scripts Added Daily/Weekly. APEX[GG]v2 UPDATED 30 Mar 2025 ( 220 Total Games ) 1945 Air Force 3D Pool Ball ACE Fighter Agent J Aliens vs Zombies Almost A Hero Ancient Allies TD Angry Birds 2 AnimA Archero Arrow Quest Attack Hole Auto Hero Awesome Tanks Ball Blast Bang Bang Rabbit Battle Strategy TD BeatStar Beyblade Rivals Bladebound Blitz: R.o.Heroes Boom Castle Boom Stick BounceMasters Bowmasters Box Head ZMD Brawl Fighter Brick Inc Bricks Breaker GB Bullet Echo Bullet Echo India CarX Highway Catapult King Chill & Kill Clan Race Clash of Destiny Conquer the Tower Conquer the Tower 2 Crossy Road Cyber Surfer DC Heroes & Villains Dead Ahead ZW Dead Raid ZS 3D Dead Trigger Dead Trigger 2 Dead Warfare Death Invasion Surv Defenders 2 Defense Legend 5 Demon Blade Devil Eater Dice Dreams Disney Heroes BM Doomsland Dragon Ball Legends Dragon POW! Dream Defense Dust Settle Dye Hard Endless Frontier Epic Stickman Faily Brakes 2 Fight for America Final Galaxy Fire Hero 2 Forged Fantasy Frozen: Free Fall Fruit Ninja 1 Fruit Ninja 2 Galaxiga Galaxy Attack SG Galaxy Shooter AFW Gems of War Grow Castle Grunt Rush Gun War Hero Blitz Hero Factory Heroes of Mavia Heroes vs Hordes Hockey All Stars 24 Honor Bound Horizon Chase Hyper Heroes Idle Hero TD Impossible Space Imposter Battle Royale Impostor Shooter MR Infinity Ops Infinity Shooter OS Injustice Gods A.U. Into the Dead 2 Island War Jewel World Museum Jurassic Monster World King of Defense Kingdom Clash Last Hero S.A Left to Survive Legion Master Lilys Garden Lonely Survivor Loot Heroes Mad Skills MX3 Magic Rampage Magic Siege Major Gun 2 MARVEL C.o.Champions Match Hit Meow Hunter Merge Archers Mini Golf King Mini TD 2 Mob Control Modern Sky War Moto Rider BRG Mr. Autofire NecroMerger NERF Superblast NFL Rivals Ninja Turtle Legends NonStop Knight 2 Otherworld Legends Pac Man 256 Panda Pop BS Perfect Kick 2 Pocket Necromancer Pokemon Quest POOKING Billliards City Pool Stars Puzzle Brawl Quest 4 Fuel R.A.C.E. Racing Legends Raid Royal 2 TD Raid Rush Raiden Fighter Ramboat 2 Real Steel Boxing Champ Realm Defense Red Siren Rival Kingdoms Robot Warfare Rodeo Stampede Royal Match Sci-Fi TD Module Shadow Gun ESW Shadow Knights Shadow Legends S.F. Shadow of Death Shadow Slayer Shadowgun Legends Shooter.io.WS SkullGirls Sky Force Reloaded Slash and Girl Slime Castle Smash Bandits Sniper 3d Sniper Strike Sonic Boom 2 Space Shooter GA Squad Alpha Star Force Steampunk Tower Steel Rage Stick Ninja 3v3 Stick War Saga Stickman Archer Online Storm Blades Street Racing 3D Stupid Zombies 1 Subway Match Survive Squad Surivor Z Swamp Attack 2 Tacticool Tank Combat WB Tank Hero Tank Stars Tap Titans 2 Tiny Gladiators 1 Tiny Gladiators 2 Top Troops Tower and Swords Tower Conquest Tower Defense BZ Tower Gunner ZS Towerlands Toy Blast Traffic Rider Transformers Bumblebee Transmute: GB Turret Defense King Undead City ZS Undead VS Demon Under Dark Unkilled Wacky Battles War Commander R.A. War Heroes War Inc : Rise War Strategy Game Warhammer 40k Tacticus Warzone Commander Wind Wings World of Artillery World Robot Boxing World Robot Boxing 2 WWE Mayhem WWII Defence Zombeast Zombie Defense Zombie Fire 3d Zombie Hunter Zombie State Zombie Warfare TDP Zombies Boom Zombtube Submitter APEXggV2 Submitted 09/24/2024 Category LUA scripts6 points
-
GameGuardian work without root So, as for work without root. This is not magic. Technical limitations were, and have remained. So it will not work anywhere and always. Actually it looks like this: 1. You put an application of virtual space (Parallel Space, VirtualXposed, Parallel Space Lite, GO multiple, 2Face and many others). 2. In it you add the game and installed GameGuardian. 3. From the virtual space application, you launch the game and GameGuardian. Actually everything. GameGuardian can be used to hack the game. Everything is simple and transparent. It was a good part of the news. Now about the bad: 1. The game has zero progress. You can not transfer the progress from the existing installation of the game, if the game itself does not provide it (through the cloud or somehow). 2. Not all games work through virtual spaces. 3. There may be another account in the game. 4. Not all functions will be available in GameGuardian. 5. On some firmware it does not work at all. If you cannot choose a proсess in GameGuardian, or get an error 105/106, then on your firmware, GG, without root, will not work. Try optimized versions of virtual spaces or another firmware or other device or get root. 6. In some virtual spaces GameGuardian does not work. What can be done in case of problems: 1. Try different virtual spaces if the problem is in them. Best option: Parallel Space. 2. Try changing the firmware. 3. Get a root and do not fool yourself. Once again: it will not work at all and always. It is possible that it will work for you and will not. Virtual spaces to run GameGuardian without root (#ct7bob3) Proper install without root - GameGuardian (#abausujp) Help: https://gameguardian.net/help/help.html#work_without_root Video-examples: Balls Bounce Free - hack balls - without root - GameGuardian, Parallel Space Bejeweled Stars: Free Match 3 - hack without root - group search - GameGuardian, GO Multiple Hack Tap Counter without root via GO Multiple on Android 7.1.1 - GameGuardian Hack Tap Counter without root via GO Multiple - GameGuardian Work without root via Parallel Space - GameGuardian Work without root via 2Face - GameGuardian Work without root via Mutiple Accounts - GameGuardian Work without root via GO Multiple - GameGuardian No root via VirtualXposed - GameGuardian (#b6l7k1qu) No root via VirtualXposed (without error 105) - GameGuardian (#bpb5835m) No root via optimized Parallel Space Lite - GameGuardian (#47glijbj) No root [from scratch] (boring and long video) - GameGuardian (#9rf9317c) No root via Dr. Clone - GameGuardian (#aft8whcy)6 points
-
So this day has come. Unfortunately we cannot delete anything, or even edit anything on this thread. I doubt even the thread owner can do that. Honestly I half expected that the devs would be aware when the thread got to this point. I agree that we should stop continue discussing on this thread or about the hack altogether. However, I doubt the devs would do anything drastic though. There are many reasons but ultimately, it comes to a point: whether taking drastic measure would do more harm or more good for their interest. AE is a niche game, and an OLD game at that, that means its players base is not big and could be dwindling faster than growing by the day. It's a gacha game but it's an OFFLINE game WITH gacha element in the spirit. The game is not competitive, no leaderboard, no pvp... and its content can be completed by everything it's been given for free. In in all honesty, all the gacha stuff actually ruins the game by making it easier with broken chars. Most of the hacks / mods simply hastens the speed that you obtain some free stuff. You cannot hack any of the paid stuff, which is the source of their income. Therefore, using hacks / mods or not, in the end, if you have enough patience you will get all the free stuff (weapons / sidegrade chars ...). They know the exploits / mods for years, and already taken measures to counter it. E.g: to enhance some of the new weapons, you have to farm horrors on the map, which spam every 6 hours. There is no place on the map that gives their drop so even using hacks, people still have to farm them normally, and thus at least keeping the "active players" / "average daily playing time" KPIs (I imagined these) in the acceptable range. They also give "hints" which items are "key" items (e.g: by making it a light source instead of a chest), so people who use mods don't accidentally pick them up. Hackers don't care if they got banned, most of them simply treat this as a side game. There may also be paid players (like me, but I stopped spending ever since SA), wiki editors among the hackers. The hackers may also spend or be converted into paid players (also me, for some occasionally SDE). Security is expensive. This is a conspiracy, but I guess some devs, or at least some alumni devs, are the ones who sell hacking services for AE. With all those points, let's say if AE is simply a PAID OFFLINE game, then once you bought it, whether you hack it or not is entirely up to you, no one tell you how to enjoy your game. However, it has a server side gacha aspect, but it's well protected and currently no hacks / mods could ever touch them. Therefore, in general hackers now are simply hacking the offline aspect of the game, and since it's non competitive, it's them ruin their own game (or making it more fun). Taking grastic measure may give the non-hacking players some joy, but I don't think it plays into their benefit. Security is expensive, if they want to protect the client side, as well as server side, they gotta pay more and if their income doesn't increase after doing so, there is no point doing it. Banning hackers may also reduce their players base, making an old niche game harder to have new players. I believe the devs are aware of the hacks / mods, but they intelligently "use" those people to their advantages (e.g: for keeping up their KPIs), that's why they intendedly leave the Nopaew exploit for too long. They ensure that hackers / modders can enjoy the game and may as well become paid players, at the same time prevent them from causing harm to paid players. Cat Express Ticket is the only middle gray area here imo. It's currently designed as a premium stuff which gives advantage to paid players. Hacking those tickets means directly tap into their income. I also fully aware of this but still decide to share the hack because my stand on this is that it should be free for everyone. There should be different way to keep the active playing time KPI (like the Cat Scratchbook). I think if the devs decide to do something, the only thing they may do is to fix the exploit that allow people hacking Cat Express Tickets. Probably the easiest is to make it an online resources, just like Chronos Stones.5 points
-
Hey I'm sorry I don't understand what you're asking, but I have clearly stated what I want to hack in the further messages if you read the whole thing, I have also stated the game name, here I'll paste the whole thing here again for you to read to understand what I'm trying to do "Additional info: I'm trying to hack the value of Total number of points on a leaderboard (I know some might say it's server side but it's quite new game and we can hack anything in the game there's not even a protection against lucky patcher in this game despite being fully multiplayer based) Now I got down to one value after earning some points in matches repeatedly, the amount you earn after a match is added to your total everytime and you progress through the leaderboard, now I have lost that value while trying something and yes that was not a Dword value but a Word value, so I might even be wrong in finding that value but I narrowed it down after 7-8 tries so I think it should be accurate I used encrypted search everytime with Auto mode (not Dword only) Update: I have figured out to search the value in Dword and it's not encrypted I but there's two of them and they both increased with the actual increase in the total points so I can't figure out which one is it, I've tried changing one but the change is reflected in both the values after I play a match and the points are added, but the change doesn't actually reflect in the game, and I don't know if it is happening at the backend and not just visually Or if there's some problem and the value can't be edited and it's server side, but what I don't understand is if it's server side how come the value is changing according to what I changed it to and not how the game is showing it For Instance- the value was 100 before, i got 22 points, the value became 122 and I found 2 values with 122, I changed one of them to 200 and the table still showed me on 122 points, so I went and played a match to see if it reflects the change after I get some more points but after I got 20 points in the match, the value showed 142 on the table, but on the game guardian search, both the values had now become 220 (200 is what I changed it to and 20 points is what I got so 220 is what the table is supposed to show if it's hacked correctly) and now there are two instances going on of the same value One in the game table where it's continuing from what it actually was i.e 142 + whatever point I get in further matches but on the game guardian search I had made for both the values, a different instance is going on where it adds whatever points I get in the next matches to 220 that was supposed to be after I hacked the value, So I don't get it please, please help" The game is GOKA Street5 points
-
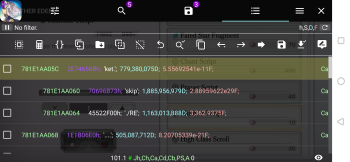
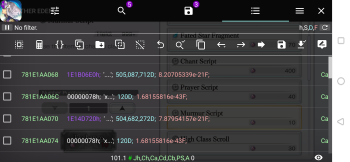
For people who're still watching this thread: I don't know to replace the selling items on Nopaew shop, but I was able to find a way to get the IDs of the items, and was successfully get the Cat Express Ticket. Basically, on this thread there are 3 things: Hack Nopaew existing items to buy a lot of it without gems: https://sbupload.com/ea247239cf61d449 Hack Red / Green keys by locking the IDs: https://pixeldrain.com/u/YmYyqKaK Hack items that are not in Nopaew shop by swapping the IDs, this is similar to the 2nd hack, except that you have to find the IDs for the items you want. I'll give the steps to get the IDs you want in step 3, but I'm too lazy to record a video. If anyone can do it successfully and have the time, please help record and upload a video. I would rather share this with everyone or let the developers fix it, than letting shameless people getting benefits from this. Here are the steps: Download and install apk from apkpure, select the armv8 architecture. This step may not be required, it's simply the version I use since I cannot download from Google Play. Follow the 2nd hack, you should save 3 variables: amount of item, the top 2 pointers (purple color). I believe that only the 2nd is needed, but haven't tested. Search for the ID of the item you want to swap, I hacked only the Cat Express Ticket, so I'll share it: Cat Express Ticket has a text ID: dungeon_ticket.skip Search using :dungeon_ticket.skip (note the semicolon in the beginning, it means text search) Refine the search with :. (semicolon, then dot) There should be 2 - 6 items left Tap on one of the results, then select Go To On this screen, you can tap on the top right corner, in the screenshot, it's where the h,S,D,F is showing. You can config how to display the values for the addresses in this screen, you should tick the Hex, String and DWORD boxes Scroll it down a few addresses, pass the end of the text ID a bit, you should see 2 pointer variables (purple) As in the screenshots, the 2 values you're looking for are 505 087 712 and 504 682 272, on my device, I can easily identify them because there are two 120D value under them, it could be different on different devices If you cannot find these ID, try with other search results Once you have the 2 values, replace the 2 pointer variables you saved before with these values, in their respective order. Like I said, probably only the latter matters but I didn't test. Continue with the hack I'm not good at Game Guardian so these steps are not that refined, and as you can see, it doesn't change the items sold in Nopaew like in the screenshots of the guys who cracked it, but the result should be the same. I hope from these steps, some smart people will refine it and share more detailed steps with everyone. You can use the same steps to hack Opus, and I guess it's possible to hack Cat Coin this way too. All the memoirs should have the prefix: job_rank_item, (e.g: job_rank_item.zodiac_fellislord, job_rank_item.zodiac_blazehero...). You can use text search to find all of them. Another way may be to unzip the downloaded APK file, there should be a localization file that would contain similar IDs. I'll leave that to other people, as for me the skip tickets are enough, as I believe the ability to skip dungeons should be free for everyone, I don't appreciate WFS lock it behind pay wall.5 points
-
Scorpius Rex Gen 2 = -708,142,142 The Spino = -858,940,3495 points
-
GameGuardian work without root Parallel Space-Multi Accounts Best choice (no error 105)! Requires Android: Android 4.0.3 (IceCreamSandwich MR1) or later. There is support for x86. Optimized version (no error 105): Download APK VirtualXposed Requires Android: Android 5.0 (Lollipop) or later. There is support for x86. Optimized version (no error 105): Download APK DualSpace Requires Android: Android 4.0.3 (Ice Cream Sandwich MR1) or later. Optimized version (no error 105): Download APK Parallel Space Lite-Dual App Requires Android: Android 4.0.3 (IceCreamSandwich MR1) or later. There is support for x86. Optimized version (no error 105): Download APK Parallel Space Pro-App Cloner Requires Android: Android 4.0.3 (IceCreamSandwich MR1) or later. There is support for x86. Optimized version (no error 105): Download APK DualSpace Blue Requires Android: Android 4.0.3 (Ice Cream Sandwich MR1) or later. Optimized version (no error 105): Download APK DualSpace Lite Requires Android: Android 4.0.3 (Ice Cream Sandwich MR1) or later. Optimized version (no error 105): Download APK ES Parallel Accounts Requires Android: Android 4.4 (KitKat) or later. Optimized version (no error 105): Download APK GO Multiple Requires Android: Android 4.0 (IceCreamSandwich) or later. There is support for x86. Optimized version (no error 105): Download APK Dr. Clone Requires Android: Android 4.4 (KitKat) or later. There is support for x86. Optimized version (no error 105): Download APK Virtual Space Requires Android: Android 4.0.3 (Ice Cream Sandwich MR1) or later. There is support for x86. Optimized version (no error 105): Download APK NoxApp+ Requires Android: Android 4.0.3 (Ice Cream Sandwich MR1) or later. There is support for x86. Optimized version (no error 105): Download APK Octopus Requires Android: Android 4.4 (KitKat) or later. Optimized version (no error 105): Download APK AppBox Requires Android: Android 4.0.3 (Ice Cream Sandwich MR1) or later. There is support for x86. Optimized version (no error 105): Download APK Multiple Space Requires Android: Android 4.1 (Jelly Bean) or later. Optimized version (no error 105): Download APK clonneapp Requires Android: Android 4.0.3 (Ice Cream Sandwich MR1) or later. There is support for x86. Optimized version (no error 105): Download APK Parallel Accounts Requires Android: Android 4.2 (Jelly Bean MR1) or later. There is support for x86. Optimized version (no error 105): Download APK APP Cloner Requires Android: Android 4.1 (Jelly Bean) or later. Optimized version (no error 105): Download APK APP Hider Requires Android: Android 4.0.3 (Ice Cream Sandwich MR1) or later. There is support for x86. Optimized version (no error 105): Download APK Calculator+ Requires Android: Android 4.0.3 (Ice Cream Sandwich MR1) or later. There is support for x86. Optimized version (no error 105): Download APK Multi Requires Android: Android 4.0.3 (Ice Cream Sandwich MR1) or later. There is support for x86. Optimized version (no error 105): Download APK 2Face - Multi Accounts Requires Android: Android 4.2 (Jelly Bean MR1) or later. There is support for x86. Optimized version (no error 105): Download APK App Hider Lite Requires Android: Android 4.0 (Ice Cream Sandwich) or later. There is support for x86. Optimized version (no error 105): Download APK Dual App Requires Android: Android 4.0.3 (Ice Cream Sandwich MR1) or later. There is support for x86. Optimized version (no error 105): Download APK Phone (Dialer Vault) Requires Android: Android 4.0.3 (Ice Cream Sandwich MR1) or later. There is support for x86. Optimized version (no error 105): Download APK Notepad Requires Android: Android 4.0.3 (Ice Cream Sandwich MR1) or later. There is support for x86. Optimized version (no error 105): Download APK VMOS Requires Android: Android 5.0 (Lollipop) or later. Google Play APKPure Clone App Requires Android: Android 4.4 (KitKat) or later. Optimized version (no error 105): Download APK You can use other virtual spaces, but there may be a 105 error. These virtual spaces are used most often and for them there are optimized versions, so we recommend using them. Complete list of all optimized virtual spaces.5 points
-
So I'm very new to game guardian and I use this on a rooted emulated Android 11 in MSI App Player I have narrowed down an encrypted value to the last, I have found the one, but I don't know how to change the value to what I want Before you suggest, I have read the few threads on this and they don't help, I didn't understand what they were trying to say, as I said I'm very new, I tried to figure out the xor or whatever it is like some guy suggested in the old thread but my encrypted value doesn't seem to work like that For eg. I have a value 1927 which has 22 as the encrypted counterpart, when it was increased by 55 and became 1982 the encrypted value became 176 further when it was increased by 547 and became 2529, the encrypted value became 10, so frankly I see no pattern here Please help me or link me to a youtube video, I've searched for hours but people touch on this issue but I haven't a solution to my exact problem P.S - I don't know what offset is, XOR is, Key is, I can just see/read and then understand it but words without demonstration mean nothing to me right now so please be cooperative and try to explain like I'm 5 or something4 points
-
4 points
-
-- set ranges -- clear results gg.searchNumber x=gg.getResulrs(gg.getResultsCount()) for i, v in ipairs(x) do v.address=v.address-0x1C end -- change 0x1C to your offset gg.loadResults(x) gg.refineNumber4 points
-
Dword search Xa -1,961,622,880;1,923,576,641;-1,440,807,966;-1,803,140,451::13 Edit first value ~A8 mov x0, #50000 You can use hex for value too, value will not decrease while it's modified. This is easiest I could do for a guide, the downside being you do need enough to spend on something for the edit to work (until I debug that too). mobizen_20241210_202541.mp44 points
-
Hi, i Create hack for this game(i dont know can i write link here to my telegram or no, that why i just add files here) BloodMoonSLA²(Libil2cpp).su.lua4 points
-
Hi Team, Is there any possibility to hack gems and other resources in this game using Game Guardian??? https://play.google.com/store/apps/details?id=com.readygo.dark.gp Please let me know. Thank You3 points
-
3 points
-
So, I’ve been trying to find a way to edit perk points, and I found some interesting stuff. 0 perk points = index 35 1 perk point = 40 (so, 1 point = 5). Sadly, this value is well protected, so you can’t edit it without ***** your perks… I also couldn’t find any pointers leading to something useful. On the other hand, I found the player's level near the perk points, and that’s also protected, if you edit it, all your perks get reset. So, don't do it lol... But a bit higher up, I found two values representing your current XP and the XP needed to level up. So, for example, if you need 300 XP to reach the next level, you can set your XP to 299 or 300 and do something to earn XP and there you go... But don’t go over that, or all your perks will reset That way, you level up normally and get 2 perk points. I've played for a bit and managed to get 30 points without any issues. Looks like a small trick to bypass the reset. I don’t have the exact pointers since memory changes depending on the device, but if you want to try maybe this will help you anyway, here’s my DWORD group search: 300D;300D;220D;220D;350D;150D;0D:41 I'll drop some pics below as proof, in case anyone's interested3 points
-
Memory Range : Anonymous Value Type : Dword For items in your backpack search the amount you have minus 10. If you have 15 of an item you search 5. If you have 5 of an item you search -5.3 points
-
I'm happy to be able to help everyone... I hope all the members here are always in good health and are always facilitated in everything. And for the game developers, especially the android platform, always have a big heart and always be facilitated in developing their game works. We are all in the process of learning... everyone plays gameguardian because they need and like the game... and I never sell game accounts to anyone. Because I also feel how difficult it is to make a game and the most entitled to get money is the creator of the game... they are big souls... and they are also just like us who started from 0.3 points
-
When we find coin, bullet, gems value in game, the address changes after we restart our game. Making it confusing for new gg Lua developers. To solve that, we use group search method. And this script will help you by: 1. Automatically generating Search code 2. Increasing search speed 3. Will find the value even if the main value changes, like bullet values which keeps changing and is not same 4. Will stores values in a table in a txt file, so you can analyse it later on (This script is meant for new gg users to make it easy for searching values using script) GG_Search_Code_Generator.lua3 points
-
For hooking void you need to call the void method by modifying another method to call it. This might be confusing for new gg users so i created an script template which allows you to hook void in gg with parameters (basic data types). With inbuild switch off code and ability to choose how many times you want to call the void method. These are the steps to use the template : 1. Download this code which i like to call method patching library , then paste it at the very top of your script 2. Now copy code for voidHook and then paste this anywhere, you can paste this in your script menu or how you would like to make your cheat active 3. Find the offset from dump.cs file or anywhere, and use those offsets to apply patches Below you can see an example of usage of this code : -- RVA: 0x1000 Offset: 0x1000 -- public static void Update() { } -- RVA: 0x2000 Offset: 0x2000 -- public void AddHealth(float health) { } HackersHouse.voidHook({ { ['libName'] = "libil2cpp", ['targetOffset'] = 0x1000, ['destinationOffset'] = 0x2000, ['parameters'] ={ { "float", 999999} }, ['repeat'] = 1, ['libIndex'] = 'auto' } }) HackersHouse.voidHookOff({ { ['libName'] = "libil2cpp", ['targetOffset'] = 0x1000, ['destinationOffset'] = 0x2000, } }) This probably has some bugs you can either report in the comments or you can come to telegram.3 points
-
3 points
-
This is great for a start! Setting the instruction to: ~A8 MOV W0, #0xFFFFFFFF Sets the leaf tokens count to the maximum value. Aside from leaf tokens, there are 3 other currencies: Bells, Caps and Complete Tickets. Bells are obvious, used to craft and purchase almost anything Caps are won (at best 50 per spin) from the slot machine by the mechanics which cost 3 Friend Powder to play, used to trade for items worth up to 10000 caps Complete Tickets are rewards for (most commonly) completing Gulliver Islands, which can be exchanged to collect either fortune cookies or limited-time event items3 points
-
3 points
-
53. Anurognathus = 2,128,082,195 53. Compsovenator = 1,015,311,692 54. Masiakasaurus = 1,995,274,011 55. Delta = 1,631,523,813 56. Dracovenator = -516,562,0603 points
-
I think it'll depend on what people are wanting/expecting. Things are possible, just within reason.3 points
-
We support only latest version. All error report about old versions will be ignored. If you have problems with the GG - create topic on help forum: https://gameguardian.net/forum/forum/14-help/, do not forget to add the necessary data: 1. Logcat shot during the problem. How to collect Logcat: https://gameguardian.net/forum/topic/7419-how-to-collect-logcat/ - REQUIRED!!! 2. Video with a problem. (if possible or applicable) Speed of solution your problem depends on availability of these data! No logcat - No help!!! Useful links: How to determine why speedhack does not work How config speedhack / How report a problem in speedhack3 points
-
I have a free, not encrypted script for this. gives HP, DMG, DODGE, CRIT DMG CRIT CHANCE etc etc. just check my profile for scripts I've posted.3 points
-
For the points, could try to rely on utf8/pointer searching... Current season :SSPPet12MainecoonPoints.amount Previous season :SSPDecor11DinoPoints.amount Believe you need at least 1 point before doing utf and pointer search. So for future events, looking for the "SSP....Points amount"should help if don't want to deal with offsets. In the attached video, my device has tagged pointers, hence the reason for 'B40000' placed in front of value for pointer search. mobizen_20240915_094600.mp43 points
-
the game is simple and easy to hack. a basic script with search,refine and edit are enough. however you can try this : TEST_RobotColony_Energy&Ore[64bit].lua3 points
-
i just need to be confirmed. try this. search = 13;2021161080::13 type = Dword memory ranges = Ca - update me later if the search gave you results.3 points
-
it would be something like this : --after search and refine local start = gg.getResults(1) local target = start[1].address + 0x990 local target2 = start[1].address + 0x29 local target3 = start[1].address + 0x34 local target4 = start[1].address + 0x32 --editing gg.setValues({ {address = target, flags = gg.TYPE_DWORD, value = 999999}, {address = target2, flags = gg.TYPE_DWORD, value = 999999}, {address = target3, flags = gg.TYPE_DWORD, value = 999999}, {address = target4, flags = gg.TYPE_DWORD, value = 999999} }) yup. adding offsets only to first result to get to another target.3 points
-
3 points
-
3 points
-
3 points
-
View File Obsidian Knight [ Script] Game Link ; Click Here Go To Download Play Store Hacks ; Hp Hack Ruby Hack Gold Hack Speed Hack Damage Hack Critical Rate & Critical Damage Hack Note; After each section you need to deactivate it and activate it again otherwise it will not work XRecorder_Edited_20250321_01.mp4 Submitter FTRMN Submitted 03/21/2025 Category LUA scripts2 points
-
2 points
-
Same method as this video. Basically you search the coin exp and timber value as 1500;124;24 and once the value comes you make a increment by one to the value you want to change. If you want to change coin. Increment 1500 by 1 and see the change in the marie order. And confirm the value. Check the new value and old value in the gg and edit that one. And thats it.2 points
-
No no, I gave the reason why I was reluctant, and I never refused I just didn't want to put it on a public forum is all, but the game is GOKA Street and do read my update I've mentioned the method of how I found it without encryption through Dword search and it still doesn't quite work2 points
-
Doesn't and can't in principle, because Lua implementation in GG is in Java (based on Luaj).2 points
-
I figured out almost ID of all items in the memoir section. It took me more than 2 days without sleeping so I decided to share it privately. If you need you can contact my discord. Now I'm going to sleep to regain my stamina. After waking up, I'll make a video how to cheat cat tickets and post it here.2 points
-
2 points
-
99.999% certain you won't be able to, resources are all controlled and verified by server.2 points
-
2 points
-
2 points
-
2 points
-
If you have problems with the GG - create topic on help forum: https://gameguardian.net/forum/forum/14-help/, do not forget to add the necessary data: 1. Logcat shot during the problem. How to collect Logcat: https://gameguardian.net/forum/topic/7419-how-to-collect-logcat/ 2. File /sdcard/Android/data/com.wood.table/files/last_run.log - copyed after exit from GG. 3. File /sdcard/Android/data/com.wood.table/files/crash.log - if exists. 4. The version of Android. 5. Screens with a problem. 6. Screens with the last tab GG after the problem occurred. Speed of solution your problem depends on availability of these data!2 points
-
Due to the fact that erroneous appeals of the form have become frequent: "My new version does not work, and the old version worked. In the new version there is an error." The following is a list of steps you must follow, otherwise your message will be ignored: 1. Try to give root rights to other applications (not GG). Root rights must be issued and operated. How to check for root in the terminal emulator If there is no root So you have problems with the root. Try to rearrange it, change its settings, or roll back to the previous version. Solve these questions in the topic of your root. 2. Install the old version of GG. It must work. If it doesn't work 3. Delete all the versions of GG, and then install the new version of GG clean. It should not work. If it works This problem was temporary, or was related to settings transferred from the old version. 4. Write logcat and video for the old version, and then for the new one. The actions there must be the same. It is desirable in general on the same process. For the old version of the error should not be. For the new - it should be. That's just after all this, you can write here with logs and videos from both versions.2 points