Search the Community
Showing results for 'Huawei mate 10'.
-
Games like this, very creative hacking can work well. I haven't installed the game, but looking at it, if you are paid out for combos, head strikes, criticals, hp left etc etc etc. Hack those. If that fails, figure out the values paid for this like that. Ex. If crit is 5 gold head strike 10 and 15 towards something else. Try doing like a 5;10;15 search and pick one and increment edit and try to see if you edit the base payout. Sometimes trying to edit the total payoit fails because game will do the 5 crits times the 5 gold for 25. you can't edit the 25 because the game is being it off of other base values. Just my input
-
bye i solve my problem my self you two instead of help to solve this version of guardian problem try to make fun of pepole 8.6.4 its cool dont have any problem and maybe you forgot something this program desighn to hack games as far as i know im not gamer but i think if you think you are top level ,which games we have negetive score for example : your xp is 10 ok you do something and its up 12 or you money, are we have -2 bilion money?????? you think becuase im newbie i dont know anything and try to destroy me/ this version has problem with any devices/Here's a word of advice humans are like bottles, when the bottle is half-full try to shake it.its sound so high but if full never you hear you to instead of try read my posts just try destroy my persenolity and teach me the math good luck Professors of Mathematics
- 26 replies
-
-3
-
Because it is not method. Because it is data type. Because data type can be signed. Because signed data type can store negative numbers. Not, problem with you. Because you do not make difference between "-" and " - ". Space you see it? With spaces around it is dash. Read next: 2–3 weeks Or you think this mean 40 and -50 people? 2 and -3 weeks? Or may be subtraction? 40-50 = -10 peoples? 2-3 = -1 weeks? ROFL. _______________________________________________ added 1 minute later But in change log of 8.6.0 written:
-
You really dont know anything about memory... Or numbers Dont use GG watch some videos how memory editing works first Numbers can start at -values you even have minus values in 3rd/4th class maths. Dword for example has the lowest value (if you see minus as lower than 0) -(4?)billion and highest 2bil nothing wrong there _______________________________________________ added 2 minutes later Ok lets have some math classes in this forum Solve all of these! -5 + 5 = ? 1 + 1 = ? -10 + 5 = ? -5 + 10 = ? If you answer all these correct congratulations you have a totally normal, functioning brain!
-
1 Dodge Dart GT 2 Audi R8 e-tron 3 Tesla Model S 4 Cadillac ATS 5 Cadillac XTS 6 Scion FR-S 7 Mini Cooper S Roadster 8 Alfa Romeo MiTo GTA 9 Audi S4 10 Nissan 370Z 11 Audi RS 3 Sportback 12 Mercedes-Benz SLS AMG Electric Drive 13 Audi TTS Coupe 14 Chevrolet Camaro GS 15 Ford Focus RS 16 Lamborghini Urus 17 Infiniti FX50 18 Lotus Exige S Coupe 19 Audi RS 4 Avant 20 Alfa Romeo 8C Competizione 21 DS Survolt 22 Aston Martin DB9 Coupe 23 Lamborghini Countach 25th Anniversary 24 Maserati GranTurismo Sport 25 Bentley Continental GT V8 26 Aston Martin V12 Zagato 27 Aston Martin V12 Vantage 28 Nissan GT-R (R35) 29 Ferrari 458 Italia 30 Ford Shelby GT500 31 Cadillac CTS-V Coupe Race Car 32 Mercedes-Benz SL 65 AMG Black Series 33 Dodge Viper SRT10 ACR-X 34 Chevrolet Corvette C7 35 McLaren 12C Spider 36 Pagani Zonda R 37 Ferrari F12berlinetta 38 Lamborghini Sesto Elemento 39 Marussia B2 40 RUF RT 12 S 41 Lamborghini Veneno 42 GTA Spano 43 RUF CTR 3 44 Ferrari FXX Evoluzione 45 Bugatti 16.4 Grand Sport Vitesse 46 Mercedes-Benz Silver Lightning 47 Koenigsegg Agera R 48 Ferrari 599XX 49 Lamborghini Gallardo LP 560-4 2013 50 Renault CLIO R.S. 200 EDC 51 BMW M6 52 Ferrari F430 53 Lotus Evora Enduro GT 54 Ferrari LaFerrari 55 W Motors Lykan HyperSport 56 Pagani Huayra 57 McLaren P1 58 SSC Tuatara 59 Ferrari Testarossa 60 SRT 2013 Dodge Challenger SRT8 61 Ford F-150 62 Hennessey Venom GT 63 Chrysler ME412 64 Ferrari FF 65 Ford 2006 GT 66 Mercedes-Benz SLS AMG GT Coupé Final Edition 67 2015 Ford Mustang 68 Jaguar C-X75 69 Mercedes-Benz CLK GTR AMG 70 Mercedes-Benz Biome 71 Peugeot Onyx 72 Jaguar F-Type R 73 Savage Rivale Roadyacht GTS 74 Mazda Furai 75 Nissan GT-R NISMO 76 SSC Ultimate Aero XT 77 Rimac Consept One 78 Savage Rivale GTR 79 Maserati MC12 80 Volkswagen W12 81 Koenigsegg One:1 82 9FF GT9 VMAX 83 Tramontana XTR 84 Felino cB7 85 Spada Codatronca 86 Arrinera Hussarya 87 Lucra L148 88 Acura NSX 2005 89 Renault DeZir 90 Ferrari F40 91 Ferrari Enzo Ferrari 92 Ferrari 612 Scaglietti 93 Ferrari F50 94 Ferrari 308 GTS 95 Ferrari 330 P4 96 Volkswagen Golf Design Vision GTI 97 BMW M3 Sedan 98 Audi R8 LMS Ultra 99 BMW M1 100 HTT Plethore LC 750 101 Lamborghini Aventador LP 700-4 102 Geely GC9 103 ONUK Sazan LM 104 Mitsubishi Lancer Evolution X 105 Chevrolet SS 106 AC 378 GT Z 107 Kepler Motion 108 McLaren 675LT 109 Bentley EXP10 Speed 6 110 McLaren P1 GTR 111 Camaro Z/28 112 Datsun 280Z 113 Shelby Cobra 427 114 SUBARU IMPREZA WRX STI 115 McLaren 570S 116 Lamborghini Huracan 117 Cadillac 16 Consept 118 McLaren F1 XP-5 119 DS 3 Racing 120 Honda S2000 121 Range Rover Evoque Coupe HSE Dynamic 122 Mercedes-Benz SLK 55 AMG 123 Toyota Supra RZ (Mark IV) 124 Nissan Skyline GT-R (R34) 125 Peugeot SR1 126 Lamgorghini Asterion 127 Mazzanti Evantra 128 Mosler GT3 129 Lamborghini Egoista 130 Renault Sport R.S. 01 131 TRION NEMESIS 132 ED Design Torq 133 Alfa Romeo 4C 134 Lamborghini Estoque 135 Rinspeed zaZen 136 Sbarro Alcador 137 Holden Coupe 60 138 Volkswagen Beetle Turbo 139 Lamborghini Miura 140 Cheverolet 2016 Camaro SS 141 Ferrari 458 Italia 142 Mosler Super GT 143 Mazda RX8 144 BMW 3.0 CSL Hommage 145 Honda Integra Type-R 146 Devel Sixteen Prototype 147 Mazda 6 148 Mitsubishi Eclipse 149 nanoFlowcell QUANT FE 150 Fenyr SuperSport 151 nanoFlowcell QUANTINO 152 Weber Faster One 153 Mercedes-AMG GT3 154 Nissan Juke Nismo 155 Jaguar XJ220S TWR Motorsport 156 Mercedes-AMG C 63 Couple 157 Jaguar F-TYPE Project 7 158 Aston Martin One-77 159 Donkervoort D8 GTO 160 Caddilac ATS-V Coupe 161 BXR Blade 162 MB GLC Coupe 163 2015 GTA Spano 164 Falcon F7 165 TVR Sagaris 166 Citroen GT 167 Icona Vulcano 168 Chevrolet Corvette C3 169 AlfaRomeo Quadrifoglio (Giulietta 2016 Veloce) 170 Mercedes CLA Racing 34 (CLA 45 AMG Rcaing Series)
-
The 1.0.1 version is buggy AND forced to use social engines to proceed the game...i dont have gamers in my fb or g+... All are my family..they not gamer...but this game at 1.0.1 forces you to login and have many friends that also have this game and play with them...in order to proceed... See the image below...as you can see the first mission is facebook login...if you do it other facebook missions will come if not...as i i didnt...its only the login mission there but in 1.0.1 version its like this: 1_login to facebook 2_send energy to 5 friends 3_ play 10 games with friends 4_ger help from friends 5_bla bla bla... Its was like a facebook game :/
-
That's not me in the videos or making them. I have someone doing them for me. I work a lot and basically have time to just hack games. I live in the US. 120F is seconds it takes to earn 10 balls. The 60 I think is time related too, it was nearby value. The way I found it. 120F search Increment edit of 100 Used all balls. Saw where the time started and went to that value to investigate nearby values. Use increase/decrease to start. Do increase every time you earn and decrease when you spend. If that gets you nothing... Do the opposite. Decrease when you earn, increase when you spend. Game that's perfect example, SAS4.
-

Android GGuardian not working on "Rolling Sky"
NoFear replied to Peaches55Haky's topic in General Android Discussion
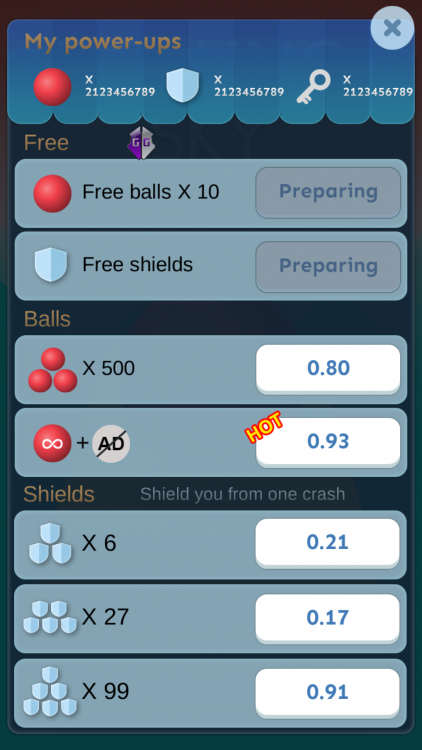
Open this file /data/data/com.turbochilli.rollingsky/shared_prefs/com.turbochilli.rollingsky.xml This is keys <string name="key_rs_yaoshi"> This is balls <string name="key_rs_shengming"> This is Shields <string name="key_rs_dun"> Paste this for the value oLAPwdXn0xxWQf20Qv6xIg== That string is 2123456789 If you want to know how. 15D;10D;10D;120F;60F:18 120 and 60 is seconds on time. 10 is how many balls are rewarded. Then copy string to other values for the game. Done. -
10-10 05:37:45.529 E/AndroidRuntime(18338): FATAL EXCEPTION: main 10-10 05:37:45.529 E/AndroidRuntime(18338): Process: com.ea.game.nfs14_row, PID: 18338 10-10 05:37:45.529 E/AndroidRuntime(18338): java.lang.NullPointerException: Attempt to invoke virtual method 'void android.widget.RelativeLayout.setVisibility(int)' on a null object reference 10-10 05:37:45.529 E/AndroidRuntime(18338): at com.firemonkeys.cloudcellapi.UserInterfaceManager$2.run(Unknown Source) 10-10 05:37:45.529 E/AndroidRuntime(18338): at android.os.Handler.handleCallback(Handler.java:739) 10-10 05:37:45.529 E/AndroidRuntime(18338): at android.os.Handler.dispatchMessage(Handler.java:95) 10-10 05:37:45.529 E/AndroidRuntime(18338): at android.os.Looper.loop(Looper.java:135) 10-10 05:37:45.529 E/AndroidRuntime(18338): at android.app.ActivityThread.main(ActivityThread.java:5264) 10-10 05:37:45.529 E/AndroidRuntime(18338): at java.lang.reflect.Method.invoke(Native Method) 10-10 05:37:45.529 E/AndroidRuntime(18338): at java.lang.reflect.Method.invoke(Method.java:372) 10-10 05:37:45.529 E/AndroidRuntime(18338): at com.android.internal.os.ZygoteInit$MethodAndArgsCaller.run(ZygoteInit.java:900) 10-10 05:37:45.529 E/AndroidRuntime(18338): at com.android.internal.os.ZygoteInit.main(ZygoteInit.java:695) 10-10 05:37:45.530 W/ActivityManager(672): Force finishing activity com.ea.game.nfs14_row/.NFSActivity This is reason of close NFS. Write to their support. Look like on open interface something going bad.
-
Implore all solution so I can open it and play it back on the game from Need For Speed: No Limits & GG. Thanks... device_info.txt 2016-10-10-05-38-04.txt
-
Need For Speed: No Limits. device_info.txt 2016-10-10-05-38-04.txt
-
Same Process, Unknown Float Decrease and increase until only very little values left <10 Optimal Edit the values only and bam only brains
-
com.nanoo.finaltaptasy.v2.playerprefs.xml fiverocks.xml All Maxed out Save ( the game basically plays itself at this point) Contains 120 Hour Gold AutoTap 10000 Stages Gold AutoTap II 120 Hour 2x Speed Multiplier All Treasure Chest Items atleast once Stage 103|1 4 Billion keys 4 Billion Awakening Stones 4 Billion Gems infinityzz Gold All Skills 100 or above All Skins for Heroes and Allies All Allies Level 125 or above Latest Weapons for all heroes atleast level 50 All Heroes Awakened to 10
-
I don't think this works on the latest version... currently there are 3 app process that is BuriedTown BuriedTown L BuriedTown push blah blah BuriiedTown DaemonServer Only BuriedTown L Produces anything. But when I did the procedure same as the video.. It produces about 8 - 11 addresses for the first part then I do the unknown search again then... results with about the same about 11 - 15 Truthfully if I can't hack this game this game has no value. The game is made to garner gazillions of in app purchase if you really want to finish this. I tried playing this game for about 10 tries. I survived for about 5-10 days max. The rng engine of this game is broken. No matter what time you go out there are times when no zombies on the way to the mall then 90% of the time.. going to your home is a pain. 3 - 5 semi permanent encounters. what the hell. If you can show me again thru a newer version that you can do this. I will not give up just yet. This game is like Day R survival. Its a In app trap game. for those want to have almost the same experience without the ***** game. try zombie live. that game is ok. better random events/.
-
10-03 05:26:30.706 27695 31595 W System.err: java.lang.IllegalArgumentException: n <= 0: -112160 10-03 05:26:30.706 27695 31595 W System.err: at java.util.Random.nextInt(Random.java:175) 10-03 05:26:30.706 27695 31595 W System.err: at com.asobimo.aurcus.d.g.d.b(Unknown Source) 10-03 05:26:30.706 27695 31595 W System.err: at com.asobimo.aurcus.d.g.d.a(Unknown Source) 10-03 05:26:30.706 27695 31595 W System.err: at com.asobimo.aurcus.d.a.o.d(Unknown Source) 10-03 05:26:30.706 27695 31595 W System.err: at com.asobimo.aurcus.h.c.a.b.a(Unknown Source) 10-03 05:26:30.706 27695 31595 W System.err: at com.asobimo.aurcus.d.a.a.a.c(Unknown Source) 10-03 05:26:30.706 27695 31595 W System.err: at com.asobimo.aurcus.y.a.a.d.a(Unknown Source) 10-03 05:26:30.706 27695 31595 W System.err: at com.asobimo.aurcus.y.a.d.a(Unknown Source) 10-03 05:26:30.706 27695 31595 W System.err: at com.asobimo.aurcus.y.n.c(Unknown Source) 10-03 05:26:30.706 27695 31595 W System.err: at com.asobimo.framework.m.n(Unknown Source) 10-03 05:26:30.706 27695 31595 W System.err: at com.asobimo.framework.k.onDrawFrame(Unknown Source) 10-03 05:26:30.706 27695 31595 W System.err: at android.opengl.GLSurfaceView$GLThread.guardedRun(GLSurfaceView.java:1525) 10-03 05:26:30.706 27695 31595 W System.err: at android.opengl.GLSurfaceView$GLThread.run(GLSurfaceView.java:1242) Something broken in game and it crashed.
-
well, all working fine now just check at java 1. SH and value change work fine. but now new problem when using both to hit,suddenly the game pull me out like crash but without notice and GG still working (but already out from game) what happen? this is the logcat. im using speed +3 and changed value. Log_2016-10-03_05-19-40.txt
-
Yeah it crash when speed hack already change speed from normal 1 to the speed u want, but it depen on the situation somehow will not crash when u change the speed like if u just check in 10 intercept u can change the speed but nothing happen. so now in my situation which one my problem? "Connect?" problem or change speed problem? (speed hack work like charm +3 for like 1 minute and will crash like the SS above)
-
i confuse about that, like this if i "just/only" check number 10 in intercept, the list of timer will full of red (it mean no green box) so nothing to check in timer. then speed hack will not work ( no crash too even u change the speed). so that u mean i should search for? sorry for asking more and need more specific. i feel something weird in our tenses english, thats why i dont understand lol xD
-
hy im new here.. The speed hack feature alway give me and error... Everytime I enable it then pop up the PTRACE_attach error permission not permitted.. Logcat 2016-10-02-22-03-22.txt
-
I USE THE ''aLogrec'' AND THIS IS THE LOG. --------- beginning of main 10-02 23:11:08.369 28063 28063 W System : ClassLoader referenced unknown path: /data/app/org.jtb.alogrec-1/lib/arm64 10-02 23:11:08.386 28063 28063 V AssetManager: New asset manager: android.content.res.AssetManager@323b543 10-02 23:11:08.388 28063 28063 V AssetManager: Making string blocks for android.content.res.AssetManager@323b543: 4 10-02 23:11:08.454 28063 28063 D AppTracker: App Event: start 10-02 23:11:12.691 28063 28063 V BoostFramework: mAcquireFunc method = public int com.qualcomm.qti.Performance.perfLockAcquire(int,int[]) 10-02 23:11:12.691 28063 28063 V BoostFramework: mReleaseFunc method = public int com.qualcomm.qti.Performance.perfLockRelease() 10-02 23:11:12.691 28063 28063 V BoostFramework: mAcquireTouchFunc method = public int com.qualcomm.qti.Performance.perfLockAcquireTouch(android.view.MotionEvent,android.util.DisplayMetrics,int,int[]) 10-02 23:11:12.692 28063 28063 V BoostFramework: mIOPStart method = public int com.qualcomm.qti.Performance.perfIOPrefetchStart(int,java.lang.String) 10-02 23:11:12.692 28063 28063 V BoostFramework: mIOPStop method = public int com.qualcomm.qti.Performance.perfIOPrefetchStop() 10-02 23:11:12.694 28063 28063 V BoostFramework: BoostFramework() : mPerf = com.qualcomm.qti.Performance@55757ab 10-02 23:11:14.363 28063 28063 D AppTracker: App Event: stop 10-02 23:11:21.358 28063 28063 D AppTracker: App Event: start 10-02 23:11:22.516 28063 28063 D AppTracker: App Event: stop 10-02 23:11:26.261 28063 28063 D AppTracker: App Event: start 10-02 23:11:29.248 28063 28063 D AppTracker: App Event: stop 10-02 23:11:31.697 28063 28063 D AppTracker: App Event: start 10-02 23:11:32.406 28063 28063 D AppTracker: App Event: stop 10-02 23:11:34.930 28063 28063 D AppTracker: App Event: start 10-02 23:11:37.229 28063 28063 D AppTracker: App Event: stop 10-02 23:11:40.074 28063 28063 D AppTracker: App Event: start 10-02 23:11:41.520 28063 28063 D AppTracker: App Event: stop 10-02 23:11:43.024 28063 28063 D AppTracker: App Event: start 10-02 23:11:43.562 28063 28063 D AppTracker: App Event: stop 10-02 23:12:27.865 28063 28063 D AppTracker: App Event: start 10-02 23:12:28.850 28063 28063 D AppTracker: App Event: stop 10-02 23:12:32.786 28063 28063 D AppTracker: App Event: start 10-02 23:12:33.613 28063 28063 D AppTracker: App Event: stop alogrec.2016-10-02-23-12-27.log _______________________________________________ added 2 minutes later start----stop----start----stop----start----stop.....etc Maybe you are right, but why? What app stop it?! Can you give me some suggestions?
-
Em....But I got the log this time. 10-02 03:31:02.665 D/BarBackgroundDrawable(2123): BarTransitions: draw: mode=MODE_TRANSPARENT, targetColor=0x0 10-02 03:31:02.666 D/BarBackgroundDrawable(2123): BarTransitions: drawColor:0x62000000 _______________________________________________ added 2 minutes later All the log look the same....
-
Oh! Nice, I got the logcat!! The log: 10-02 03:31:02.665 D/BarBackgroundDrawable(2123): BarTransitions: draw: mode=MODE_TRANSPARENT, targetColor=0x0 10-02 03:31:02.666 D/BarBackgroundDrawable(2123): BarTransitions: drawColor:0x62000000 _______________________________________________ added 2 minutes later I got the logcat just now.
-
wow, thanks mate. i never knew it's this easy. hmm, too bad i have deleted that brother in arms but i'll just start over thanks a lot both of you @Enyby @geribaldi
-
Currency/fame Dword union search 1;444442:5 Goto one of the results. Scroll up until you start seeing 10 digit values. The first 444442 value isn't gold, the 2nd one is (will be roughly 444442 + your current gold qty) . Just edit that value, in video I do value below it. Game doesn't save it it after close and reopen. For item hack, goto a shop (when you find one). Goto and item that has like 5. Dword search 5. Buy one, search 4. Etc etc etc etc Edit and freeze to 999 or whatever. Goto address and scroll and find the other items and freeze qty to 999. Now go through and put a check next to the item id (directly above the qty). Edit the series of values with increment of 1. This will help maximize finding more items faster. 20001 is the start of basic items (materials and stuff). 30001 is the start of weapons.
-
Thanks. Mate.
- 12 replies
-
-2