Leaderboard
Popular Content
Showing content with the highest reputation since 11/14/2025 in all areas
-
KA_MASTER_SCRIPT.lua KA_ITEM_DATA.lua - script for both 32bit and 64bit - tested in 32bit and 64bit game, version 2.61 [IMPORTANT] - download and place both files in the same directory/folder - any feedback are much welcome5 points
-
Memory Range : Anonymous Value Type : E:Double Just simple search, refine & edit for each resource.2 points
-
Awesome script! DC Heroes and Villains worked like a charm. Please kindly make one for Harry Potter Puzzles and Spells. A script for infinite moves would be nice. Thanks in advance! Keep up the great work2 points
-
yup. new dinos came with new game update. in some region, update show up earlier in their Playstore than other. always remember to check for an update before trying anything new.2 points
-
2 points
-
Scolosaurus ; 378,474,081 Skoolasaurus ; 1,564,722,760 Skoonasaurus ; 1,869,980,8742 points
-
I just found my player id and the base still exist with the hacked castle i am amazed that it wasn't banned For anyone curious to check it out #Q8j8YRG9P The way i did it back then i didn't havz root so i used virtualxposed and cloned the app and then i ran the speedhack function slowed the game down. Then i changed the elixir value to 10000 (you can do this by searching the elixir as Dword) quickly built the castle before the game syncs with the server and reboots and then placed the castle somewhere, the intresting part is that the server does indeed check that elixir value is wrong and that you shouldn't have the castle built but it does not check to verify that the coordinates are still the same. But for this modern version i run into ptrace protection which idk if it is due to newer versions of the game or because i am using root (using magisk) instead of virtually cloning the app.2 points
-
2 points
-
yeah. maybe. I'd like to hack this game again anyways and maybe add some new hacks after I've learned some new things.. but right now I'm currently working on a big project. maybe after I'm done with that.2 points
-
1 point
-
1 point
-
View File Online Mega Script v06 UPDATED 18 Nov 2025 [ 239 ] Total Games 1945 Air Force 3D Pool Ball ACE Fighter Agent J Aliens vs Zombies Almost A Hero Ancient Allies TD Angry Birds 2 Angry Birds Family Angry Birds Friends Angry Birds Match3 AnimA Archero Arrow Quest Attack Hole Auto Hero Awesome Tanks Ball Blast Bang Bang Rabbit Battle Strategy TD BeatStar Beyblade Rivals Bladebound Blitz: R.o.Heroes BOOM Castle Boom Stick BounceMasters Bowmasters Box Head ZMD Brawl Fighter Brick Inc Bricks Breaker GB CarX Highway Catapult King Chill & Kill Clan Race Clash of Destiny Combat Cruiser Conquer the Tower Conquer the Tower 2 Crossy Road Cyber Surfer Cyberpunk Hero DC Heroes Villains Dead Ahead ZW Dead Raid ZS 3D Dead Trigger Dead Trigger 2 Dead Warfare Death Invasion: Surv. Defenders 2 Defense Legend 5 Demon Blade Devil Eater Dice Dreams Disney Heroes BM Doomsland Dragon Ball Legends Dragon POW! Dragon Titan Uprising Dream Defense Dungeon Slasher Dust Settle Dye Hard Endless Frontier Epic Stickman EventHorizon Frontier Faily Brakes 2 Fight for America Final Galaxy Fire Hero 2 Forged Fantasy Frozen: Free Fall Fruit Ninja 1 Fruit Ninja 2 Galaxiga Galaxy Attack SG Galaxy Shooter: AFW GEARS: W.M. Gems of War Grow Castle Grunt Rush Gun Run A.S.S. Gun War Hero Blitz Hero Factory Heroes of Mavia Heroes vs Hordes Hockey All Stars 24 Honor Bound Horizon Chase Hyper Heroes Idle Hero TD Idle Monster TD Impossible Space Imposter Battle Royale Impostor Shooter MR Infinity Ops Infinity Shooter OS Injustice Gods A.U. Into the Dead 2 Island War Jewel World Museum Jurassic Monster World King of Defense 3 Kingdom Clash Last Hero S.A. Left to Survive Legend of Gladiator Legion Master Lilys Garden Lonely Survivor Loot Heroes Mad Skills MX3 Magic Rampage Magic Siege Major Gun 2 MARVEL C.o.Champions Match Hit Mecha Fortress Merge Archers Mini Golf King Mini TD 2 Mob Control Modern Sky War Moto Rider BRG Mr. Autofire NecroMerger NERF Superblast NFL Rivals Ninja Turtle Legends NonStop Knight 2 Pac Man 256 Panda Pop BS Perfect Kick 2 Pocket Necromancer Pokemon Quest POOKING - B.C. Pool Stars Puzzle Brawl Quest 4 Fuel R.A.C.E. Racing Legends Raid Royal 2 TD Raid Rush Raiden Fighter Ramboat 2 Real Steel Boxing Champ Realm Defense Red Siren Rival Kingdoms Robot Warfare Rodeo Stampede Royal Kingdom Royal Match Sci-Fi TD Module Shadow Gun ESW Shadow Knights Shadow Legends S.F. Shadow of Death Shadow Rival Shadow Slayer Shadowgun Legends Shooter.io.WS SkullGirls Sky Force Reloaded Slash and Girl Slime Castle Smash Bandits Sniper 3d Sniper Strike Sonic Boom 2 Space Quest Space Shooter GA Squad Alpha Star Force Steampunk Tower Steel Rage Stick Ninja 3v3 Stick War Saga Stickman Archer Online Storm Blades Street Racing 3D Stupid Zombies 1 Subway Match Subway Surfers Summoners Greed Survive Squad Survivor Z Swamp Attack 2 Tacticool Tank Combat Tank Hero Tank Stars Tap Titans 2 TDS Tower Dest Surv Timeline Up Tiny Gladiators 1 Tiny Gladiators 2 Top Troops Tower and Swords Tower Conquest Tower Defense BZ Tower Def Galaxy V Tower Gunner ZS Tower King Towerlands Toy Blast Traffic Rider Transformers Bumblebee Transmute: GB Turret Defense King Undead City ZS Undead VS Demon Under Dark Unkilled Wacky Battles War Commander R.A. War Heroes War Inc : Rise War Regions War Strategy Game Warhammer 40k Tac. Warzone Commander Wild Castle Wind Wings World of Artillery World Robot Boxing World Robot Boxing 2 WWE Mayhem WWII Defence Zombeast Zombie Defense Zombie Fire 3D Zombie Hunter Zombie State Zombie Warfare TDP Zombies Boom Zombtube Submitter APEXggV2 Submitted 09/24/2024 Category LUA scripts1 point
-
well.. this script isn't built for newbies. this forum has scripts for all skill levels. new users to advanced. anyways. in a month or two I should have a new script. need to rebuild this one from scratch. it's version 22 now, and everytime I update I just add more to it.. it's a big mess right now.. new script will have more features be more user friendly. have an extensive help section etc.1 point
-
-- Il2CppGG by LeThi9GG require("Il2CppGG") -- Usage Instructions: -- This script demonstrates the core functionalities of Il2CppGG, a Lua-based toolkit for inspecting and manipulating Il2Cpp structures in GameGuardian. -- It covers image retrieval, class searching, method and field access, value modification, class dumping, and memory hooking. -- Prerequisites: Ensure GameGuardian is running and the target application uses Il2Cpp. Load this script in GameGuardian for execution. -- Note: Addresses and values are examples; adapt them to your specific game or application. -- For detailed API documentation, refer to the project's README.md or wiki. -- Example: Retrieve Image by Name -- Description: Fetches an Il2Cpp image (assembly) by its name. Use Il2Cpp.Image() without arguments to get all images. local Assembly = Il2Cpp.Image("Assembly-CSharp") -- Retrieves the "Assembly-CSharp" assembly. -- Example: Find Class within an Image -- Description: Searches for a class in the specified image using namespace and class name. Namespace can be nil for root-level classes. local PlayerScript = Assembly:Class(nil, "PlayerScript") -- Parameters: (namespace, classname) -- Alternative: Find Class by Name, Address, or Index -- Description: Directly searches for a class by name (recommended to use GetIndex() for performance optimization). --local PlayerScript = Il2Cpp.Class("PlayerScript") --print(PlayerScript:GetIndex()) -- Outputs the class index for faster future access. -- Example: Find Methods in a Class -- Description: Retrieves a specific method by name or lists all methods with GetMethods(). local LateUpdate = PlayerScript:GetMethod("LateUpdate") -- Finds the "LateUpdate" method. local addPoints = PlayerScript:GetMethod("addPoints") -- Finds the "addPoints" method. -- Example: Find Fields in a Class -- Description: Retrieves a specific field by name or lists all fields with GetFields(). local points = PlayerScript:GetField("points") -- Finds the "points" field. -- Alternative: Find Field by Name or Address -- Description: Global search for a field by name or direct address. --local points = Il2Cpp.Field("points") -- Searches globally by name. -- Alternative: Find Method by Name or Address -- Description: Global search for a method by name or direct address. --local AddPoints = Il2Cpp.Method("AddPoints") -- Searches globally by name. -- Example: Modify a Field Value -- Description: Locates an instance of the class and sets a new value for the field. local obj = PlayerScript:GetInstance() -- Retrieves instances of the class. points:SetValue(obj, 1000) -- Sets the "points" field to 1000 in the instance. -- Example: Dump Class to C# Format -- Description: Outputs the class structure in C# syntax for reverse engineering purposes. --print(PlayerScript:Dump()) -- Dumps the class definition, including fields, methods, and offsets. -- Hooking Examples -- Description: Demonstrates memory hooking for real-time modifications using the Hook module. -- Hooks allow intercepting and altering method calls, parameters, and fields. -- Hook a Field via a Method (e.g., hook "points" field using "LateUpdate" method) -- Description: Modifies the field value every time the method is called. local _LateUpdate = LateUpdate:field() -- Initializes hook on the method for field modification. _LateUpdate:setValues({{offset = points.offset, flags = "int", value = 9999}}) -- Sets the field to 9999. gg.sleep(10000) -- Pauses for 10 seconds to observe the effect. _LateUpdate:off() -- Disables the hook and restores original behavior. -- Hook Parameters of a Method (e.g., hook parameters of "addPoints") -- Description: Alters the parameter values passed to the method. local _addPoints = addPoints:method() -- Initializes hook on the method for parameter modification. _addPoints:param({{param = 1, flags = "int", value = 999999}}) -- Sets the first parameter to 999999. gg.sleep(10000) -- Pauses for 10 seconds. _addPoints:off() -- Disables the hook. -- Hook a Method Call (e.g., call "addPoints" from "LateUpdate") -- Description: Injects a call to another method with custom parameters during execution. local _addPoints = LateUpdate:call()(addPoints) -- Initializes hook to call "addPoints" from "LateUpdate". _addPoints:setValues({{param = 1, flags = "int", value = 999}}) -- Sets the parameter for the called method. gg.sleep(10000) -- Pauses for 10 seconds. _addPoints:off() -- Disables the hook. Il2CppGG Telegram Youtube1 point
-
does anyone know how to hack an event like clash of titans & decoding dreadactylus ??1 point
-
it's sometimes better for make a tutorial or something on how to use you method patcher script and explain how it actually works and what methods are because most people that use GG i assume don't know how that stuff works. Like the whole method patching only seem to have got some fame here a couple of years ago. But many members of the forum actually use basic GG search features (unknown search or something) and hope to find the value that way. Like for example you can't expect someone that is just trying to hack gold understands how to make use of such way of cheating the game. In my opinion. So yeah. My point is, make video tutorials and explain more detailed how the stuff works and why it works, like that more people can make use of a good script. Like i see it many times now, good scripts that don't get the attention it deserves because obviously people don't have any familiarity with what it is even about. It's not like this is a Reverse engineering forum, it is a forum on which people make request about cheating games and get help or something with the GG tool. So i think that at least if a script is made that is doing more then just modifying some values to hack some gold or whatever then people should be properly introduced to the functionality and purpose of the script within a forum like this in which the audience is most likely not coming from some serious technical background. Otherwise all we doing is feeding or ego in a place where it's really irrelevant.1 point
-
Thanks ! Now i can enjoying play this game without frustrating unable/lack of skill to cheat using gameguardian. You are the best ! Cheers1 point
-
new script posted (live update don't have to download anything) has jewel hack. the prices of summon will give you 1000000 jewels. and improved speed hack...1 point
-
Version V 06
22,943 downloads
UPDATED 03 Dec 2025 [ 242 ] Total Games 1941 Air Attack 1945 Air Force 3D Pool Ball ACE Fighter Agent J Aliens vs Zombies Almost A Hero Ancient Allies TD Angry Birds 2 Angry Birds Family Angry Birds Friends Angry Birds Match3 AnimA Archero Arrow Quest Attack Hole Auto Hero Awesome Tanks Ball Blast Bang Bang Rabbit Battle Strategy TD BeatStar Beyblade Rivals Bladebound Blitz: R.o.Heroes BOOM Castle Boom Stick BounceMasters Bowmasters Box Head ZMD Brawl Fighter Brick Inc Bricks Breaker GB Bullet Echo CarX Highway Catapult King Chill & Kill Clan Race Clash of Destiny Combat Cruiser Conquer the Tower Conquer the Tower 2 Crossy Road Cyber Surfer Cyberpunk Hero DC Heroes Villains Dead Ahead ZW Dead Raid ZS 3D Dead Trigger Dead Trigger 2 Dead Warfare Death Invasion: Surv. Defenders 2 Defense Legend 5 Demon Blade Devil Eater Dice Dreams Disney Heroes BM Doomsland Dragon Ball Legends Dragon POW! Dragon Titan Uprising Dream Defense Dungeon Slasher Dust Settle Dye Hard Endless Frontier Epic Stickman EventHorizon Frontier Faily Brakes 2 Fight for America Final Galaxy Fire Hero 2 Forged Fantasy Frozen: Free Fall Fruit Ninja 1 Fruit Ninja 2 Galaxiga Galaxy Attack SG Galaxy Shooter: AFW GEARS: W.M. Gems of War Grow Castle Grunt Rush Gun Run A.S.S. Gun War Hero Blitz Hero Factory Heroes of Mavia Heroes vs Hordes Hockey All Stars 24 Honor Bound Horizon Chase Hyper Heroes Idle Hero TD Idle Monster TD Impossible Space Imposter Battle Royale Impostor Shooter MR Infinity Ops Infinity Shooter OS Injustice Gods A.U. Into the Dead 2 Island War Jewel World Museum Jurassic Monster World King of Defense 3 Kingdom Clash Kingdom Wars Merge Last Hero S.A. Left to Survive Legend of Gladiator Legion Master Lilys Garden Lonely Survivor Loot Heroes Mad Skills MX3 Magic Rampage Magic Siege Major Gun 2 MARVEL C.o.Champions Match Hit Mecha Fortress Merge Archers Mini Golf King Mini TD 2 Mob Control Modern Sky War Moto Rider BRG Mr. Autofire NecroMerger NERF Superblast NFL Rivals Ninja Turtle Legends NonStop Knight 2 Pac Man 256 Panda Pop BS Perfect Kick 2 Pocket Necromancer Pokemon Quest POOKING - B.C. Pool Stars Puzzle Brawl Quest 4 Fuel R.A.C.E. Racing Legends Raid Royal 2 TD Raid Rush Raiden Fighter Ramboat 2 Real Steel Boxing Champ Realm Defense Red Siren Rival Kingdoms Robot Warfare Rodeo Stampede Royal Kingdom Royal Match Sci-Fi TD Module Shadow Gun ESW Shadow Knights Shadow Legends S.F. Shadow of Death Shadow Rival Shadow Slayer Shadowgun Legends Shooter.io.WS SkullGirls Sky Force Reloaded Slash and Girl Slime Castle Smash Bandits Sniper 3d Sniper Strike Sonic Boom 2 Space Quest Space Shooter GA Squad Alpha Star Force Steampunk Tower Steel Rage Stick Ninja 3v3 Stick War Saga Stickman Archer Online Storm Blades Street Racing 3D Stupid Zombies 1 Subway Match Subway Surfers Summoners Greed Survive Squad Survivor Z Swamp Attack 2 Tacticool Tank Combat Tank Hero Tank Stars Tap Titans 2 TDS Tower Dest Surv Timeline Up Tiny Gladiators 1 Tiny Gladiators 2 Top Troops Tower and Swords Tower Conquest Tower Defense BZ Tower Def Galaxy V Tower Gunner ZS Tower King Towerlands Toy Blast Traffic Rider Transformers Bumblebee Transmute: GB Turret Defense King Undead City ZS Undead VS Demon Under Dark Unkilled Wacky Battles War Commander R.A. War Heroes War Inc : Rise War Regions War Strategy Game Warhammer 40k Tac. Warzone Commander Wild Castle Wind Wings World of Artillery World Robot Boxing World Robot Boxing 2 WWE Mayhem WWII Defence Zombeast Zombie Defense Zombie Fire 3D Zombie Hunter Zombie State Zombie Warfare TDP Zombies Boom Zombtube1 point -
Script is posted. Auto-Win, Gold, No Ads, Game Speed. https://gameguardian.net/forum/files/file/4052-online-mega-script-v06/1 point
-
1 point
-
View File Speed Hack Finder Finds game speed value (multiplier) for 100% Unity games / 20% Non-Unity. Edit Float as a multiplier (2.0=2×speed, 10.0=10×speed, 0.25=1/4 speed) Option to copy full code so you can paste into your own scripts. Submitter APEXggV2 Submitted 12/02/2025 Category Tools1 point
-
Version 1.3_1
2,346 downloads
Get information about loaded library inside memory. * Pros - Parsed ELF Structure, Program Header, Dynamic Segment, Symbol * Cons - Section Header are not parsed, because it not loaded into memory. - Only 32-Bit Elf Supported. * Thanks to: - @Enyby * Use cases: - PinOut Hax - Injection References: [1] https://en.wikipedia.org/wiki/Executable_and_Linkable_Format [2] http://phrack.org/issues/59/8.html (I need to create elf parser before getting through. xD)1 point -
For dynamic addresses the base address is a pointer which you obtained through a chain of pointers or an address from a group search or combination of both, which you can use to calculate the distance from base address to address of the gold value. If your not familiar with it you can use scripts from the forum. For games made in Unity, try using field offset finder. On other game engines perhaps try using the chainer script. Maybe this video helps you:1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 point
-
1 Coin 2 Ruby 3 Mosaic(Fragment) 4 Hints 5 XP 10 Katana 11 Shuriken 12 Fan 13 Petard 14 Bomb(Horoku) 15 Arrows 16 Spikes(Makibishi) 17 Boomerang 18 Battering ram(Kikkosha) 19 Mortar 20 Sushi 30 Wood 31 Stone 32 Steel 33 Charcoal 34 Gunpowder 35 Iron sand 36 Chemicals 37 Treasure 38 Gold ingot 39 Wooden beam 40 Coffee beans 41 Wooden plank 42 Salmon 43 Tuna 44 Cup of coffee 45 Spices 46 Ramen 47 Curry 48 Anchor 49 Pearl 50 Treasure map lvl.1 51 Treasure map lvl.2 52 Treasure map lvl.3 53 Treasure map fragment lvl.1 54 Treasure map fragment lvl.2 55 Treasure map fragment lvl.3 56 Smuggler's map 57 Treasure map fragment lvl.4 58 Smuggler's map 59 Smuggler's map 60 Backpack 61 Axe 62 Pickaxe 63 Torch 64 Magnifier 65 Scarab 66 Maneki-neko 67 Pirate's compass 68 Oil lamp 69 Porcelain vase 70 Eye of Horus 71 Hannya mask 72 Templar helm 73 Turquoise skull 74 Dancing Shiva 75 Pirate hat 76 Ship in a bottle 77 Black pearl 78 Shogun's mortar(Sho-gun) 79 Shogun's katana 80 Hotei statuette 81 Necklace for Haruka 82 Guild codex 83 Guild banner 84 Guild supplies 85 Helmet 86 Dagger 87 Trigonometry 88 Emerald tablet 89 Historical library 90 Treasure map lvl.4 91 Safe 92 Astrolobe 93 Tetrachloroaurate 94 Telescope 95 Cinema projector 96 Barometer 97 Hat of concentration 98 Flamethrower 99 Solver-1 prototype 100 Dinar 101 Paper 102 Silk 103 Dates 104 Olive oil 105 Honey 106 Kimono 107 Ninja suit 108 Samurai armor 109 Date cake 110 Glass 111 Elixir of insight 112 Firework 113 Mechanical arithmetic logic unit(MALU) 114 Punched card 115 Pot of gold 116 Titanium parts 117 Grimoire 118 Madness grenade 119 Ring for a hero lvl.4+ 120 Potion of healing 121 Potion of energy 122 Potion of healing lvl.2 123 Potion "Ambrosia" 124 Potion "Berseker rage" 125 Ancient page 126 Drum(Taiko) 127 Ultraviolet cherry 128 Meteoric iron 129 Meteoric steel 130 Avocado 131 Steamobile 132 Gears 133 Mechanism 134 Blueprint 135 Wheat 136 Flour 137 Rice 138 Onigiri 139 Flatbread 140 Crypto-coin 141 Mushroom 142 Emerald tablet shard 143 Throwing knife(Kunai) 144 Greek grenade 145 Catacombs map 146 Catacombs map fragment 147 Very old scroll 148 Reagent 149 Catalyst 150 Smoothie 151 Poke 152 Cherry bun 153 Mushroom rice(Bento) 154 Sword for a hero lvl.1 155 Sword for a hero lvl.2 156 Sword for a hero lvl.3 157 Armor for a hero lvl.1 158 Armor for a hero lvl.2 159 Armor for a hero lvl.3 160 Shield for a hero lvl.1 161 Shield for a hero lvl.2 162 Shield for a hero lvl.3 163 Ring for a hero lvl.1 164 Ring for a hero lvl.2 165 Ring for a hero lvl.3 166 Mandrake root 167 Key 168 Mechanical spider 169 Baklava 170 Potion of mental power 171 Potion of mental power 172 Thread 173 Ariadne's thread(red) 174 Throwing net 175 Ring for a hero lvl.4 176 Sword for a hero lvl.4 177 Dragon teeth 178 Egg 179 Soy sauce 180 Mayonnaise 181 Teriyaki salmon 182 Fried eggs 183 Marinated eggs 184 Potion of mental power 185 Horn 186 Synthetic fertilizer 187 Mandra-cola 188 Shield for a hero lvl.4 189 The Ring of the Dark Lady 190 Throwing(Axe) 191 Throwing(Web) 192 Mental power 193 Golden egg 194 Woodland strawberry 195 Mercury 196 Porcini mushroom 197 Titanium 198 Ginkgo biloba 199 Herbs 200 Ship 201 Message in a bottle 202 Caravan 203 Firework 204 Airship 205 Throwing(Single arrow) 206 Flamethrower(for combat) 207 Train 208 Throwing? 209 Grappling hook 210 Cinnabar 211 Arsenopyrite 212 Smoothie#2 213 Jam 214 Salamander hide 215 Salamander velour 216 Armor for a hero lvl.4 217 Potion of mental power 218 Balm 219 Bedroll 220 Muffin 221 Porcini pasta 222 Key(Green) 223 Metal detector 224 Empty bottles 225 Familiar? 226 Familiar? 227 Familiar? 230 Pet? 231 Pet? 232 Pet? 233 Pet? 235 Tofu 236 Inarizushi 237 Ariadne's thread(blue) 238 Ariadne's thread(brown) 239 Ariadne's thread(green) 241 Quartz 242 Red Crystal 243 Green Crystal 244 Blue Crystal 245 Violet Crystal 246 Diamond 247 Bamboo 248 Zen fountain(Shishi-odoshi) 249 Enzyme 250 Milk 251 Soft cheese 252 Vintage cheese 253 Sword for a hero lvl.4+ 254 Armor for a hero lvl.4+ 255 Shield for a hero lvl.4+ 256 Red diamond 257 Goat 258 Coffee ice cream 259 Pizza Diavola1 point
-
Today I spent the entire Halloween event thanks to some tricks I learned. I'll show you how to buy contracts at low prices (spoiler: the last contract, the Butcher's, is worth 150k coins) - that's a lot! That's why I'm going to show you how I bought the third contract for 20 coins, and this applies to all contracts. Besides that, I got the camp skins just by trading items. That has been uploaded many times here, but it's necessary for you to know. I don't have that video yet, let me know if you want it. screen-20251028-104415.mp41 point
-
Version 2.0.0
556 downloads
Version: 4.2.3 Combat Menu • Zero Energy Cost • Instant Spawn • Global AoE Radius • Global Shield Boost • Global Critical Boost Player Menu • HighDamage • God Mode • Mission XP Boost • Item Bonus Extreme • Ad Coin Boost Bus Menu • Bus Invincibility • Bus Damage Boost • Minigun Damage Boost • Unlock Bus Upgrade1 point -
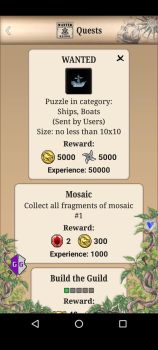
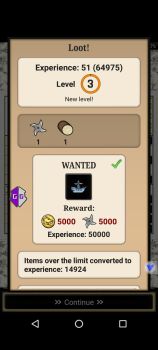
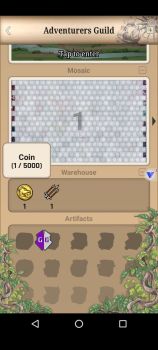
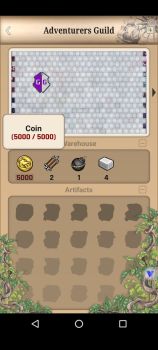
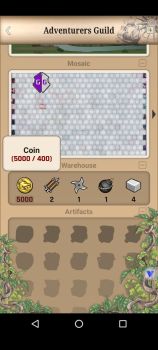
the limit wasnt permanent. it reset after game restart as shown in the pic below. Coin limit is at 400 in the Warehouse. red text indicate its over the limit. but the edited Coin value obtained from the Quest remain and can be use normally. search a single value(400) then use increment edit to find the right one. must change the limit first before completing the quest. otherwise the excess value will turn into experience.1 point
-
1 point
-
instead of just random edit, you can change the item value to any value you like. use XOR key = 375066 Record_2025-10-24-05-08-04_9c29c5ced1cbbaf4012f4db13dfab3bd.mp4 this also can be apply for searching items value which ever the easier item value ~ XOR key 375066 = XOR value in the memory1 point
-
value edited isnt visual but can actually be obtained after quest completed. but there is a capacity limit for each items in the warehouse. the excess will be converted to experience. need to edit the limit first in order to get all the items(normal Dword search) the value stay even the limit reset after restart.1 point
-
1 point
-
Heroic level up without shards VID_20250925203244.mp4 Dino must at Level 40 = 3;10;Dino HP::171 point
-
1 point
-
I finally found out a way to run GG on Android 10.0, it works 100% . I'm using Android 10 and running GG without root. You can guys should download VMOS. It's a virtual space that runs on version 5.1 so it enables the running of Game Guardian without root. Make sure you enable the "root option" upon installation. You can watch the video on my YouTube channel (Game Lovers Villa) - The download links are provided in the video. Please subscribe as you watch1 point
-
1 point
-
View File CAR PARKING MULTIPLAYER CAR PARKING MULTIPLAYER SCRIPT SCRIPT FEATURES- COIN HACK and GOLD HACK I will explain how to use HOW TO USE COIN HACK? 1) GO TO MAIN MENU 2) APPLY COIN HACK 3) CLICK ON THAT INSTAGRAM FOLOW BUTTON +$5000 4) YOUR HACK IS DONE HOW TO USE GOLD HACK? 1) GO TO MAIN MENU 2) GO TO DRIVER 3) GO TO ANIMATIONS (down left) 4) NOW BUY 2 showing -99999 ( if didn't show restart and apply again) 5) now buy after buying 2 items , now buy -214 like something value 6) boom your gold is hacked FOLLOW US ON TELEGRAM TO GET LATEST UPDATES https://t.me/TheGamecheaters IN THE CHANNEL YOU CAN CONTACT THE CREATOR EASILY Submitter CALISTA Submitted 04/24/2024 Category LUA scripts1 point
-
How to set Game Guardian with Apktool M for Android 14 Compatibility This guide will walk you through editing SDK target of Game Guardian (GG) using Apktool M to ensure compatibility with newer Android versions "Android 14" Hey Darklord aka OREW here again --------------------------------------- 1. Download Required Tools: Game Guardian (GG) Apktool M --- 2. Decompile the Game Guardian APK: Open Apktool M. Locate the GG APK file. Select the GG APK, then click "Decompile" and wait until the process completes. --- 3. Edit the apktool.json File: Open the decompiled GG folder. Locate and open the apktool.json file. Find lines 29 and 30: "minSdkVersion": "10", "targetSdkVersion": "22" Change both versions to: "minSdkVersion": "24", "targetSdkVersion": "24" Example of apktool.json After Editing: { "apkFileName": "GameGuardian.101.1_src.apk", "PackageInfo": { "forcedPackageId": "127", "renameManifestPackage": null }, "doNotCompress": [ "resources.arsc", "png", "res/raw/ydwsh" ], "compressionType": false, "sparseResources": true, "version": "2.4.0-241015", "sharedLibrary": false, "VersionInfo": { "versionName": "101.1", "versionCode": "16142" }, "UsesFramework": { "ids": [1], "tag": null }, "unknownFiles": {}, "apkFilePath": "/storage/emulated/0/Download/GameGuardian.101.1.apk", "compactEntries": false, "isFrameworkApk": false, "sdkInfo": { "minSdkVersion": "24", "targetSdkVersion": "24" } } Save and exit the file. --- 4. Recompile the Modified APK: In Apktool M, click the "Compile" button at the top of the folder structure. Check the box for "Use aapt" and press OK. Wait for the process to finish. --- 5. Install the Recompiled APK: After recompilation, press the "Install" button. When prompted, grant root access through Magisk Manager or KernelSU Manager (as applicable). Open GG, select the default configuration, and enable the "Install from unknown sources" permission if required. --- 6. Handle Installation Issues: If GG doesn't install directly after the package name randomizer process, follow these steps: Exit and navigate to: Android > data > com.catch_.me_.if_.you_.can_ (GG data folder) > cache > tmpe.apk This tmpe.apk file is the new GG package. In Apktool M, open it and select "Quick Edit." Set the Main SDK and Target SDK versions to 24. Press "Save", install the new package, and you're done! --- Enjoy using Game Guardian on your device! ^_^1 point
-
if people that knowns somethings about something shares, it's like opening a pandora box at first i thought i can just EOL revolted on v3 and move on, but after watching a series of video by some internet security and such, the dude name in youtube was LiveOverflow, i thought myself, what if i can tamper the connection, so i tried to bruteforce the encryption first, but then i realize this is not a normal data transfer, so i look up the source and as expected it's encrypted, and since then ive been snooping the request and such, but like always, just if the community just like Unknowncheats, this game will be dead eons ago. anyway, i found a modifier that modify the search quantity accidentally when i trying to find alternative for leveling let's say you search a pharmacy, you'll get 1-4 amount of certain meds, and since i found this modifier, you know can get 10K+ i also found alot of multiplayer settings, unprotected, just as it, Gift Limit, Chat cooldown, banned items, opening gift cooldown, i kinda want to scrap the idea to try replay attacks on websocket connection. cuz like i dont find anything special from it, i'll try to unban myself without slash command by mod, if i do, i wouldnt be surprised i think i should make YT tutorials for day r hacking lmao imma start with caps, cuz all i see on yt is "this hacks doesn't work after 766, devs patched it"1 point
-
View File Minecraft Script Lua Includes Speed Hack Air Walk Air Jump Jump Blocks No Fall Damage Fly Mode God Mode Fast Sprint Enlarged HitBox High FOV Teleport Mode Broken Arm Mode Speed 2 Jump Boost Head Rotate If you find any bugs report to me asap so I can fix them Note some Options may need to be turned on more than once to get a result Teststed & Working On Lattest Version Of Minecraft Submitter LUCKYDAY999 Submitted 01/17/2021 Category LUA scripts1 point
-
Binary scripts with corrupted or invalid headers interfere with application development. For this reason: Starting with GG 87.0, a variety of warnings and notifications are displayed ("Invalid binary script header"). In future versions of GG, such scripts will not be executed. Uploading such files to the forum is blocked. All scripts that allow you to create binary scripts with damaged headers will be deleted. You can use a script that replaces the header: Lua header fixer (#8vs58ae4) If this does not help, write to the author of the script. To users of scripts: write to script authors so that they do not spoil the headers. To script writers: Don't mess with the headers. If you want to indicate authorship, there are messages, toasts, and other ways. The file header is not a means of self-expression. If your encryptor / compiler has been deleted, you can remove the creation of corrupted headers from it and upload it as a new file.1 point
-
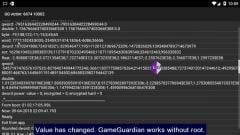
GameGuardian work without root So, as for work without root. This is not magic. Technical limitations were, and have remained. So it will not work anywhere and always. Actually it looks like this: 1. You put an application of virtual space (Parallel Space, VirtualXposed, Parallel Space Lite, GO multiple, 2Face and many others). 2. In it you add the game and installed GameGuardian. 3. From the virtual space application, you launch the game and GameGuardian. Actually everything. GameGuardian can be used to hack the game. Everything is simple and transparent. It was a good part of the news. Now about the bad: 1. The game has zero progress. You can not transfer the progress from the existing installation of the game, if the game itself does not provide it (through the cloud or somehow). 2. Not all games work through virtual spaces. 3. There may be another account in the game. 4. Not all functions will be available in GameGuardian. 5. On some firmware it does not work at all. If you cannot choose a proсess in GameGuardian, or get an error 105/106, then on your firmware, GG, without root, will not work. Try optimized versions of virtual spaces or another firmware or other device or get root. 6. In some virtual spaces GameGuardian does not work. What can be done in case of problems: 1. Try different virtual spaces if the problem is in them. Best option: Parallel Space. 2. Try changing the firmware. 3. Get a root and do not fool yourself. Once again: it will not work at all and always. It is possible that it will work for you and will not. Virtual spaces to run GameGuardian without root (#ct7bob3) Proper install without root - GameGuardian (#abausujp) Help: https://gameguardian.net/help/help.html#work_without_root Video-examples: Balls Bounce Free - hack balls - without root - GameGuardian, Parallel Space Bejeweled Stars: Free Match 3 - hack without root - group search - GameGuardian, GO Multiple Hack Tap Counter without root via GO Multiple on Android 7.1.1 - GameGuardian Hack Tap Counter without root via GO Multiple - GameGuardian Work without root via Parallel Space - GameGuardian Work without root via 2Face - GameGuardian Work without root via Mutiple Accounts - GameGuardian Work without root via GO Multiple - GameGuardian No root via VirtualXposed - GameGuardian (#b6l7k1qu) No root via VirtualXposed (without error 105) - GameGuardian (#bpb5835m) No root via optimized Parallel Space Lite - GameGuardian (#47glijbj) No root [from scratch] (boring and long video) - GameGuardian (#9rf9317c) No root via Dr. Clone - GameGuardian (#aft8whcy)1 point
-
1 point
-
The unique program with an excellent set of features. Distinctive features: support x86 and x64 devices and emulators (BlueStacks, Droid4X, Genymotion etc.); support Android 5+ and 6+; deceleration / acceleration speed games (ARM devices only); direct and fuzzy search; multiple fuzzy search for equality; search encrypted XOR values; search for fractional values; modify all the values found at once; show search progress; advanced filtering of search results; search value not only for equality but also in terms of more / less. Unique features GameGuardian Availability Search for encrypted values. Group Search supports all data types, including float and xor. Search in the application code. Changing the application code. Support of "data type" xor, are often used to protect the values of the changes in the games. Displays an unlimited number of search results, the main thing that you have enough memory. Filtering the search results according to various criteria. Autofill on values change. The ability to enter data in hexadecimal. The rollback feature values change if you do not need. Extended freeze values. Advanced application settings system. Viewing the game screen, without closing the program interface. The input history. Unique in-memory data storage system that allows you to store data in memory and avoid crashes the program when available memory runs out. Speedhack runs on x86 devices. Speedhack runs on android 7. speedhack Function: time jump, which allows you to go forward in time, to the exact distance. Unique speedhack configuration allows fine-tune the desired intercept timers in the game without touching unnecessary. The unique masking system unable to detect the fact of installing and running the program for the protection systems of most games. Extremely high stability. Active support. Constant updating. Localization into many languages. Special tricks against some common protective systems.1 point













.thumb.jpg.2985ee18f499743e5bfceb4f03deca48.jpg)