Search the Community
Showing results for tags 'il2cpp'.
-
Version 2.4.1
813 downloads
Patcher Patcher is a game guardian library for patching memory address, it provides a simple interface and handle on/off state of patching. Installation Download the latest version of patcher from here and add it to your project. You can also load the latest version of Patcher from the cdn using the following code. local _, Patcher = pcall(load(gg.makeRequest("https://pastebin.com/raw/wz1sfmWF").content)) Usage Make sure to place the Patcher.lua file in the same directory as your script. local Patcher = require("Patcher") local il2cpp = Patcher.getBaseAddr("libil2cpp.so") local libunity = Patcher.getBaseAddr("libunity.so") local p = Patcher.new({ title = "Custom Title", }) p:add({ name = "Damage Multiplier", address = il2cpp + 0x18643A8, patch = "01 04 A0 E3 1E FF 2F E1r", }) p:add({ name = "HP Multiplier", address = libunity + 0x1864F88, patch = "01 04 A0 E3 1E FF 2F E1r" }) p:run() For more information about how to use the library, please check the repo -
Regarding the listening function on Gameguardian, my idea is to parse the symbol table of libil2cpp.so through the ELF file structure and parse out some il2cpp api functions in the native layer, such as il2cpp_method_get_name, and its ARM assembly segment is generally LDR X0, [X0,#0x18] ~A8 RET When many functions are called, the pointer of the function instance will be X0. When assembled by il2cpp_method_get_name, the function name string is read through the offset of 0x18. Then we modify the function flow. Since many called functions will execute the assembly of this API function, we can write a unique tag value and actively tag ourselves when the function passes by. Then we can monitor which functions are called by searching for this tag value. call LDR X10, [PC,#0xC] STR X10, [X0,#0x40] ~A8 RET 983466571 We use the LDR instruction to load the tag 983466571 into the useless register X10, and then use the STR instruction to write the tag value to 0x40 of X0 (the function pointer, which is also the first bit of the function structure). Then when the function is called, When this API is executed, it actively exposes itself by writing the STR mark so that I can monitor it. Of course, don’t forget to make up for it LDR X0, [X0,#0x18] ~A8 RET Otherwise it will cause the game to crash The above are some of Shenmi’s ideas, and the gglua tool with this function has been written and can be used.
-
-
View File il2cpp’s most powerful method name template This lua is only for ARM64This is an il2cpp class name and method name template, the most powerful template that surpasses everyone, because it actively calls the il2cpp native api, allowing the game to find its own method name by itself, instead of gg search, without any search. , the speed surpasses everything, and the accuracy surpasses everything. It can only be used for ARM64. You will definitely encounter some problems when using it. You can ask me in private message. Submitter shenmi Submitted 01/15/2025 Category Templates
-
- Method to hide Album
- arm64-v8a
-
(and 2 more)
Tagged with:
-
View File Patcher Patcher Patcher is a game guardian library for patching memory address, it provides a simple interface and handle on/off state of patching. Installation Download the latest version of patcher from here and add it to your project. You can also load the latest version of Patcher from the cdn using the following code. local _, Patcher = pcall(load(gg.makeRequest("https://pastebin.com/raw/wz1sfmWF").content)) Usage Make sure to place the Patcher.lua file in the same directory as your script. local Patcher = require("Patcher") local il2cpp = Patcher.getBaseAddr("libil2cpp.so") local libunity = Patcher.getBaseAddr("libunity.so") local p = Patcher.new({ title = "Custom Title", }) p:add({ name = "Damage Multiplier", address = il2cpp + 0x18643A8, patch = "01 04 A0 E3 1E FF 2F E1r", }) p:add({ name = "HP Multiplier", address = libunity + 0x1864F88, patch = "01 04 A0 E3 1E FF 2F E1r" }) p:run() For more information about how to use the library, please check the repo Submitter MAARS Submitted 02/18/2023 Category Tools
-
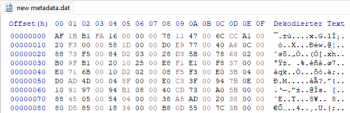
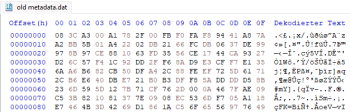
A new major update of the game 'Night of the Full Moon' is coming out soon, which kinda caught my attention. I was able to mod an older version of the game (1.5.1.37), but that approach doesn't work for the newest version anymore (1.5.1.50). Here's my analysis: -The developers use their own anti-tamper solution called 'HProtect'. It (was?) responsible for decrypting the metadata, and it also force closed the game if any changes were detected. -They updated HProtect, and I wasn't able to figure out what it does now. -The metadata in the old version of the game was obviously obfuscated, but the one in the new version is not, since the 4 magic bytes are valid (I uploaded some screenshots). -The il2cpp.so binary seems to be valid and not encrypted at all. Things that I tried so far: -Using the zygisk il2cppdumper didn't work (dump.cs hasn't been created), but it did work with the old version of the game though. -Dumping via GameGuardian worked, but the output was identical to the file you get from the apk. -il2cppdumper gives me the "System.IO.EndOfStreamException: Unable to read beyond the end of the stream" error when trying to dump. -il2cppInspector says "could not verify the integrity of the metadata file or accurately identify the metadata sub-version" when selecting the metadata file. -Libdumper didn't work (also produced the identical output). I'm kinda lost at this point, it would be great if someone could help me out with this. Also, please let me know if I forgot to include something. Thanks in advance Metadata from the newest version.rar Metadata from the older version.rar Newest version of HProtect.rar Older version of HProtect.rar
-
View File SuperSusDumper this script can help you dump Super Sus. file will be saved in '/sdcard/Download' Telegram: https://t.me/TDL0VE TelegramGroup: https://t.me/TdLove_Chat_Group Submitter TdLove Submitted 10/29/2024 Category Tools