-
Posts
658 -
Joined
-
Last visited
-
Days Won
25
Content Type
Profiles
Forums
Downloads
Gallery
Posts posted by MAARS
-
-
The index is not always the same so to avoid some runtime error you can make it dynamic
local function getBaseAddr(lib) local rangeList = gg.getRangesList(lib) for _, v in ipairs(rangeList) do if v.state == "Xa" then return v.start end end end local libanogs = getBaseAddr("libanogs.so") gg.alert(tostring(libanogs + 0x129fc4)) -- "0x129fc4" is your function address -- The function will be located at libil2cpp.so + function address.
0 -
write this in QWORD
00 00 A0 E3 1E FF 2F E1r
1 -
public class SaveGameManager : MonoBehaviour [Address(RVA = "0x129E248", Offset = "0x129D248", VA = "0x129E248")] public static int getTotalMoney() // return high ammount
Unlimited money
public class CarProperties : MonoBehaviour [Address(RVA = "0x12B34E4", Offset = "0x12B24E4", VA = "0x12B34E4", Slot = "47")] public virtual bool getIsPremium() // return false
make paid cars available to buy with in game money instead of real money
1 -
Hi, your game is protected with CodeStage anti cheat, thankfully this is one of easy one to bypass.
First you will need to dump the game using Il2cppDumperGUI any or il2cpp dumper of your choice.
next you're going to look for CodeStage detection methods.
note those StartDetection methods, most have some overload if you want to be safe you will need to bypass them all, but it is rare that the game use them all, but better be safe than sorry.
so here is the list and overloads.
CodeStage.AntiCheat.Detectors.ObscuredCheatingDetector StartDetection(); // 0x00818a3c static CodeStage.AntiCheat.Detectors.ObscuredCheatingDetector StartDetection(System.Action callback); // 0x00818ce8 CodeStage.AntiCheat.Detectors.ObscuredCheatingDetector StartDetectionInternal(System.Action callback); // 0x00818b70 System.Void StartDetectionAutomatically(); // 0x00819058 static CodeStage.AntiCheat.Detectors.SpeedHackDetector StartDetection(); // 0x008190e0 static CodeStage.AntiCheat.Detectors.SpeedHackDetector StartDetection(System.Action callback); // 0x0081948c static CodeStage.AntiCheat.Detectors.SpeedHackDetector StartDetection(System.Action callback, System.Single interval); // 0x008194e4 static CodeStage.AntiCheat.Detectors.SpeedHackDetector StartDetection(System.Action callback, System.Single interval, System.Byte maxFalsePositives); // 0x0081954c static CodeStage.AntiCheat.Detectors.SpeedHackDetector StartDetection(System.Action callback, System.Single interval, System.Byte maxFalsePositives, System.Int32 coolDown); // 0x008195c4 CodeStage.AntiCheat.Detectors.SpeedHackDetector StartDetectionInternal(System.Action callback, System.Single checkInterval, System.Byte falsePositives, System.Int32 shotsTillCooldown); // 0x008192dc System.Void StartDetectionAutomatically(); // 0x00819a54 static System.Void StartDetection(); // 0x00818648 static System.Void StartDetection(System.Action<System.String> callback); // 0x008186b0 System.Void StartDetectionAutomatically(); // 0x008187e8
there is two way to bypass those.
1. you can just patch each of them using the "NOP RET/BX LR" opcode.
2. allocate memory page and replace and replace those method with there respective StopDetection, that mean when the game call StartDetection instead it will call StopDetectionNow for GEMS/XP/Gold/Health
Note at this stage since you have already bypassed the AntiCheat editing your stat wont trigger anything. but you need first to understand how ObscuredInt work.
note every obscure value you see on your screen is a fake value. you should not edit it directly but the edit the hidden value using the crypto key. Here bellow is what you need to remember about the structure.public struct ObscuredInt [FieldOffset(Offset = "0x0")] private int currentCryptoKey; [FieldOffset(Offset = "0x4")] private int hiddenValue; [FieldOffset(Offset = "0xC")] private int fakeValue; (what you see on screen)
What you see on your screen is the fakeValue. to edit it you will need to edit the hidden value.
Here is how to. (note offset might varies depending on the game and version so you better have the latest dump and check the correct offset)When you find an ObscureInt fakeValue. you need to go back into the base pointer so in this case: fakeValue.Address - 0xC which will bring you to currentCryptoKey copy the value of currentCryptoKey in (DWORD) then offset to currentCryptoKey.address + 0x4 this will bring you to the hiddenValue now to edit this to your desired value you need to perform XOR (exclusive OR) to your desired value using the currentCryptoKey as a key. you can do that inside gg, you type the value then apply the xor key
That it you are done. you can edit any ObscureInt using this method.
now specially for your game there are some vulnerabilities that i found you can exploit to edit your stat and in game money. there are some method likes:
public class game_manager : MonoBehaviour [Address(RVA = "0xA65A94", Offset = "0xA65A94", VA = "0xA65A94")] public void gem_plus(int gem) [Address(RVA = "0xA65890", Offset = "0xA65890", VA = "0xA65890")] public void gold_plus(int gold) [Address(RVA = "0xA64DFC", Offset = "0xA64DFC", VA = "0xA64DFC")] public void iron_plus(int iron)
All those share the almost the same structure so i will be giving an example only for gem_plus

In this de-compiled function gem_plus, you can see that they are loading the value of the ObscureInt field
public ObscuredInt gem_total; // 0x2CC
into the variable puVar1 which later on they add it value + param_2 which is the gem parameter, to instantiate a new ObscureInt from that sum. the result of that sum will be stored into the register W0, so all we have to do is just hijack this register and change the value to what we want. here is a video of how to do that.
This method do not trigger the anti cheat cause the game is writing legit value for us. also if you want to move large value you might want to explore the MOVZ instruction or you can allocate a memory page and spam multiple ADD instruction like this
add w0, w0, #500000000add w0, w0, #500000000
add w0, w0, #500000000
add w0, w0, #500000000
add w0, w0, #500000000....
Last thing for gems you will need to stay on the main screen like in the video when you start the game cause that function trigger only there.
I kinda like the game i might continue working on it and update this thread4 -
2 hours ago, NoFear said:
Gdb, rwatch on value. If editing value with GG triggers a ban or local error, just rwatch value to see everything reading it. Sometimes you'll get many results, just have to go through and find the one that triggers ban. Ideally, it'd be a branch to one anti cheat function. Then you could xref that function, NOP all the branches to it, or RET the function.
Thanks, gotta get my hands on gdb tho, never used it
0 -
11 hours ago, NoFear said:
is will skip the area that woul
12 hours ago, NoFear said:Without checking dump or going into ida, just simple debug to find what's reading gems.
Armv8
Offset: 11A6C34
Edit to
B [PC,#0x80]
This will skip the area that would trigger ban.
Then this
Offset: 113DD74
Mov w22 (large value).
This is what writes value after it does a check. So you can force it to write something excessive after it checks value (I don't think you have limit since the check will never branch to ban, see attached image).
You could apply this same concept to any value, just set read watch to see what is checking it, then bypass the ban. Could check dump or something to see what the offset is part of or maybe what it branches to.
Interesting, this technique could be also useful with my other project, which tool you use to monitor memory access ?
0 -
1 hour ago, nok1a said:
Did not knew that, thanks!
constant variable are made so you dont have to memorize these constant value ? why would you want to type the value ?
0 -
public class DataBaseScript : MonoBehaviour public int Quest_Get_Gem_Normal(int Quest_numb) // return a high amount if you want (like 100K) public bool Quest_Bool_Normal(int Quest_numb) // return true to redeem quest reward infinitly
In game quest -> dungeon
4Million so far and no ban.
Off Topic:
I recommend using this app Swift Backup to backup the game if you are trying something that you think might get you banned. so if you get banned you can just restore previous game state and continue. since the ban is local nothing from a serverYou get banned around 18 Millions
0 -
After a lot of hours working on this game, i conclude that the game is actively subtracting your earning - your total spent gems to detect if you cheated or not. all you have to do is just disguise your coins as it have been earned.
for that you can edit reward etc.., here i edited gems you get when unlocking book skin, you can also edit quest reward if you want
public class DataBaseScript : MonoBehaviour public int Get_Gem_Book_by_Rare(int rare_)
0 -
-
5 hours ago, imperialx said:
Ohh manual ban, by the way I was using auto clicker with gg script given up there and speed hack at 4 . I completed all the maps and was farming rank dungeon.
What is your architecture? 64bit or 32bit ? I think the ban can be ignored, but I still can't get myself banned right now, so you might want to test the bypass
0 -
3 hours ago, imperialx said:
Got ban again now in its written t_back instead of gems bruh if we can just block anticheat if possible
How long did it take to get you banned ? what hack you where using ? i am having a hard time trying just to trigger the ban.
also there is no anti cheat. just some control flow made by the dev himself. the ban seem to be manual coming from the server the game just perform some check if you are banned or not. i will be able to do more check on i get banned
0 -
Number Guess
A simple number guessing game. The player must guess the number that the game has randomly selected. The game has 4 difficulty levels: Easy, Medium, Hard, and Insanity. The player has a limited number of attempts to guess the number. The game will tell the player if the number is higher or lower than the guess.
-
Submitter
-
Submitted04/05/2024
-
Category
0 -
-
to encrypt
in Help
Only use ASCII if you want your code to be compatible with everything
0 -
On 3/31/2024 at 9:22 PM, nok1a said:
I don't see any protection though. But thanks for posting the class. It avoided me dumping the game and made it no struggle for find. I dunno why field offset finder doesn't work, perhaps a script needs to be made. Offset 0x20
I don't know if encryption is the right word but. The memory is not disposed how it should be for a il2cpp game. Address are weird. That why any field offset finder won't work. I did manual search like for 3pmon until I gave up. Note since I had also Frida I used the exact runtime address with the goto tool with gg but that did not help at all the address lead somewhere that not the field offset
1 -
-
what does twains mean ? i would understand better if you said like every 5 minute/sec/days etc...
0 -
There are already many topic about this this you should check them
0 -
Welcome among us
0 -
give the game link and describe what you are trying to do
0 -
15 hours ago, HEROGAMEOfficial said:
Offset is distance. Example:
A = 2
B = 8
Offset is 6.
In completion, offset can also be negative:
knowing the addresses of both
A = 2
B = 8
The distance from A to B is 6
The distance from B to A is -61 -
15 hours ago, _yourram said:
[ @MANDO01 ] is there any command by which if the 1st result is empty then the script starts searching the 2nd search results directly?
You have just to check if the search result is empty.
if (gg.getResultsCount() <= 0) then -- end
And i see some logic issue with the script15 hours ago, _yourram said:local t = gg.getResults(10)
Here you call getResult 10 but you called getResult 1 just earlier, would make sense if you skipped the 1st result but you did not
15 hours ago, _yourram said:t[i].flags = 16
are u using flags 16 and 4 in some place on purpose or you missed ? i am a little bit confused in this context
15 hours ago, _yourram said:gg.removeListItems(t)
why are u calling remove list item knowing you just called addListItem just earlier with the same list ?
ps: you can still optimize that operation by using one big loop that wrap everything, as i think about it it might not improve performance since you will be making the same number or search but for sure it will reduce code and repetition0 -
local utf8 = require("utf8") local chars = {} for i = utf8.codepoint("A"), utf8.codepoint("Z") do table.insert(chars, utf8.char(i)) end local ch = gg.choice(chars, 0, "Choose a letter to spam") print("You chose: " .. chars[ch])
1 -
On 11/21/2023 at 2:43 PM, Ardit19 said:
I found a way to do it from first value to go to 3rd without needing to save all results. You say that the code you attached will load first three results but I want to load only the third for example. If there is a way if not I will stick to the solution I found.
The code @MC874 provided actually do what you described except that index is 3 since lua table index start at 1 instead of 0
2

.jpg.28a7e3592021a57b8ef85be6fb6ebcd2.jpg)

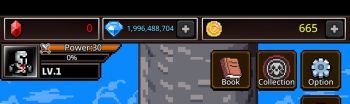







How i change/bypass the limit of score/point
in Help
Posted · Edited by MAARS
Is the game fully offline ? if not i will not recommend doing this, that just a way to flag yourself as a cheater if the game actually keep player record which is mostly the case if your game is online/semi online