Leaderboard
Popular Content
Showing content with the highest reputation since 04/19/2023 in Posts
-
GameGuardian work without root So, as for work without root. This is not magic. Technical limitations were, and have remained. So it will not work anywhere and always. Actually it looks like this: 1. You put an application of virtual space (Parallel Space, VirtualXposed, Parallel Space Lite, GO multiple, 2Face and many others). 2. In it you add the game and installed GameGuardian. 3. From the virtual space application, you launch the game and GameGuardian. Actually everything. GameGuardian can be used to hack the game. Everything is simple and transparent. It was a good part of the news. Now about the bad: 1. The game has zero progress. You can not transfer the progress from the existing installation of the game, if the game itself does not provide it (through the cloud or somehow). 2. Not all games work through virtual spaces. 3. There may be another account in the game. 4. Not all functions will be available in GameGuardian. 5. On some firmware it does not work at all. If you cannot choose a proсess in GameGuardian, or get an error 105/106, then on your firmware, GG, without root, will not work. Try optimized versions of virtual spaces or another firmware or other device or get root. 6. In some virtual spaces GameGuardian does not work. What can be done in case of problems: 1. Try different virtual spaces if the problem is in them. Best option: Parallel Space. 2. Try changing the firmware. 3. Get a root and do not fool yourself. Once again: it will not work at all and always. It is possible that it will work for you and will not. Virtual spaces to run GameGuardian without root (#ct7bob3) Proper install without root - GameGuardian (#abausujp) Help: https://gameguardian.net/help/help.html#work_without_root Video-examples: Balls Bounce Free - hack balls - without root - GameGuardian, Parallel Space Bejeweled Stars: Free Match 3 - hack without root - group search - GameGuardian, GO Multiple Hack Tap Counter without root via GO Multiple on Android 7.1.1 - GameGuardian Hack Tap Counter without root via GO Multiple - GameGuardian Work without root via Parallel Space - GameGuardian Work without root via 2Face - GameGuardian Work without root via Mutiple Accounts - GameGuardian Work without root via GO Multiple - GameGuardian No root via VirtualXposed - GameGuardian (#b6l7k1qu) No root via VirtualXposed (without error 105) - GameGuardian (#bpb5835m) No root via optimized Parallel Space Lite - GameGuardian (#47glijbj) No root [from scratch] (boring and long video) - GameGuardian (#9rf9317c) No root via Dr. Clone - GameGuardian (#aft8whcy)13 points
-
9 points
-
Hi @chrislin2k, Currently Game Guardian haven't been updated for quite some time. There's 3 thing that you can do: - Use Virtual Machine: VPhoneGaGa, VMos Pro, x8SandBox, F1 VM - Change Game Guardian SDK version to 33 using: APK Editor - Force Install Game Guardian using ADB: adb install --bypass-low-target-sdk-block gameguardian.apk9 points
-
So I believe this game already has all your dice rolls calculated for your account. Server already knows where you'll land on your next roll. I believe minigames, outcomes are already determined before you even land on them (pre determined like all your dice rolls). Wouldn't it be nice to know how much your next roll would've won, then you would've done multiplier to maximize....... Well, that's just what this is going to be about. To see your future rolls/minigames, you'll have game open and switch to offline mode. Using a root file explorer navigate to here: /data/data/com.scopely.monopolygo/files/ Each turn you take a file is generated, something like this: 48d4483b70674c02951ddfd3a289f5d7.ca When you reconnect, it'll send these and get your account synced. If you get prompted no connection, you can click back to remove message and tap roll really quick. So you can roll indefinitely and write down/log all your rolls. Even if you stay on one board logging it all. When you switch to a new board, your dice roll continues. Not like a new board, new roll pattern. When you land on a spot that gives a good size reward. You can delete those .ca files, close, restart game online and use max multiplier to really bonus up those wins. Bank Heist, don't think you had a chance of picking the right combination.... No matter where you selected, what flips over, will always be same when you play it again. So if I flipped coin, ring, cash, cash, ring, cash. When I go to play again, it's going to be that exact order. See attached video. I'm honestly really disappointed in my findings with this developer. It feels like a scam of a game and you're not really "playing". It's basically scripted and if you do x1, x5, x10 at ideal times, that's about the only user "input" that seems to have a chance on the outcome. mobizen_20230426_211255.mp49 points
-
7 points
-
So what I'm finding, I think should be noted and possibly call out the developer on the matter. I'll probably share what I know and how it can benefit within a couple days or so... I'm not really impressed though with the developer. It feels like a scam of a game, you'll all see after I do more tests.7 points
-
Armv8 C80E42B8r;081540FDr::3809 Edit 28008052r;E803679Er And if you want to set so you can claim all without playing (set number of keys collected). Offset (Version 6.9.5) 3FBCA54 Edit 00FA8052r6 points
-
6 points
-
6 points
-
No luck... Definitely have put some time into figuring out dice. And not making any progress. Still trying though.6 points
-
https://www.mediafire.com/file/6qowx7yuctayo3t/rr3_race_mode.v11.4.1.4.9.x64.bin.lua/file6 points
-
Working on it.... Their is some stuff in the dump, that if server didn't kick back an error, would be perfect.6 points
-
View File RR3 v12.0.1 Reset bonus price (VP) Reset bonus price (VP) in all rounds, both architectures And open all expired rounds. This script uses pointer chains, so it may not work with another game version. Tested on NOX 7.1.2 (32bit) and tablet with Android 10 (x64) and VirtualXposed. reset-vp.mp4 Submitter Count_Nosferatu Submitted 04/29/2023 Category LUA scripts5 points
-
5 points
-
5 points
-
5 points
-
5 points
-
This post cannot be displayed because it is in a forum which requires at least 1 post to view.
-
5 points
-
New version 11.5.1.4.1.x64 released! Added 'Search mode' Changed menu5 points
-
Sorry for the delay on this y'all, I was away for a bit. The issue was affecting new uploads because of security changes we recently made. Should be resolved now.5 points
-
Hi, your game is protected with CodeStage anti cheat, thankfully this is one of easy one to bypass. First you will need to dump the game using Il2cppDumperGUI any or il2cpp dumper of your choice. next you're going to look for CodeStage detection methods. note those StartDetection methods, most have some overload if you want to be safe you will need to bypass them all, but it is rare that the game use them all, but better be safe than sorry. so here is the list and overloads. CodeStage.AntiCheat.Detectors.ObscuredCheatingDetector StartDetection(); // 0x00818a3c static CodeStage.AntiCheat.Detectors.ObscuredCheatingDetector StartDetection(System.Action callback); // 0x00818ce8 CodeStage.AntiCheat.Detectors.ObscuredCheatingDetector StartDetectionInternal(System.Action callback); // 0x00818b70 System.Void StartDetectionAutomatically(); // 0x00819058 static CodeStage.AntiCheat.Detectors.SpeedHackDetector StartDetection(); // 0x008190e0 static CodeStage.AntiCheat.Detectors.SpeedHackDetector StartDetection(System.Action callback); // 0x0081948c static CodeStage.AntiCheat.Detectors.SpeedHackDetector StartDetection(System.Action callback, System.Single interval); // 0x008194e4 static CodeStage.AntiCheat.Detectors.SpeedHackDetector StartDetection(System.Action callback, System.Single interval, System.Byte maxFalsePositives); // 0x0081954c static CodeStage.AntiCheat.Detectors.SpeedHackDetector StartDetection(System.Action callback, System.Single interval, System.Byte maxFalsePositives, System.Int32 coolDown); // 0x008195c4 CodeStage.AntiCheat.Detectors.SpeedHackDetector StartDetectionInternal(System.Action callback, System.Single checkInterval, System.Byte falsePositives, System.Int32 shotsTillCooldown); // 0x008192dc System.Void StartDetectionAutomatically(); // 0x00819a54 static System.Void StartDetection(); // 0x00818648 static System.Void StartDetection(System.Action<System.String> callback); // 0x008186b0 System.Void StartDetectionAutomatically(); // 0x008187e8 there is two way to bypass those. 1. you can just patch each of them using the "NOP RET/BX LR" opcode. 2. allocate memory page and replace and replace those method with there respective StopDetection, that mean when the game call StartDetection instead it will call StopDetection Now for GEMS/XP/Gold/Health Note at this stage since you have already bypassed the AntiCheat editing your stat wont trigger anything. but you need first to understand how ObscuredInt work. note every obscure value you see on your screen is a fake value. you should not edit it directly but the edit the hidden value using the crypto key. Here bellow is what you need to remember about the structure. public struct ObscuredInt [FieldOffset(Offset = "0x0")] private int currentCryptoKey; [FieldOffset(Offset = "0x4")] private int hiddenValue; [FieldOffset(Offset = "0xC")] private int fakeValue; (what you see on screen) What you see on your screen is the fakeValue. to edit it you will need to edit the hidden value. Here is how to. (note offset might varies depending on the game and version so you better have the latest dump and check the correct offset) When you find an ObscureInt fakeValue. you need to go back into the base pointer so in this case: fakeValue.Address - 0xC which will bring you to currentCryptoKey copy the value of currentCryptoKey in (DWORD) then offset to currentCryptoKey.address + 0x4 this will bring you to the hiddenValue now to edit this to your desired value you need to perform XOR (exclusive OR) to your desired value using the currentCryptoKey as a key. you can do that inside gg, you type the value then apply the xor key That it you are done. you can edit any ObscureInt using this method. now specially for your game there are some vulnerabilities that i found you can exploit to edit your stat and in game money. there are some method likes: public class game_manager : MonoBehaviour [Address(RVA = "0xA65A94", Offset = "0xA65A94", VA = "0xA65A94")] public void gem_plus(int gem) [Address(RVA = "0xA65890", Offset = "0xA65890", VA = "0xA65890")] public void gold_plus(int gold) [Address(RVA = "0xA64DFC", Offset = "0xA64DFC", VA = "0xA64DFC")] public void iron_plus(int iron) All those share the almost the same structure so i will be giving an example only for gem_plus In this de-compiled function gem_plus, you can see that they are loading the value of the ObscureInt field public ObscuredInt gem_total; // 0x2CC into the variable puVar1 which later on they add it value + param_2 which is the gem parameter, to instantiate a new ObscureInt from that sum. the result of that sum will be stored into the register W0, so all we have to do is just hijack this register and change the value to what we want. here is a video of how to do that. This method do not trigger the anti cheat cause the game is writing legit value for us. also if you want to move large value you might want to explore the MOVZ instruction or you can allocate a memory page and spam multiple ADD instruction like this add w0, w0, #500000000 add w0, w0, #500000000 add w0, w0, #500000000 add w0, w0, #500000000 add w0, w0, #500000000 .... Last thing for gems you will need to stay on the main screen like in the video when you start the game cause that function trigger only there. I kinda like the game i might continue working on it and update this thread4 points
-
[ Introduction ] Hi @everyone, in recent times, Android has just released version 14, which includes some SDK restrictions. The requirements are that apps should at least be under SDK version 24+, or else installation fails. Another problem is that Game Guardian hasn't been updated for years (March 22, 2021, since the last update), a total of 2 years. I understand that life can be unbothered sometimes, and I hope there's some confirmation regarding this instead of intending it as an "unforseeable future" kind of thing. I've seen a rising number of these issues on Help, General Discussion, and in other possible sections of the forum. I recommend anyone who has a newer device or just recently updated to Android 14 to follow this topic. Here, I propose several possible solutions regarding this issue: [ Main Course ] You can bypass SDK enforcement using shell commands, which you need to install Game Guardian manually through command line. You can achieve this through ADB: Android Debug Bridge or Termux: Terminal for Command Line application. This tutorial will split into 2: { ADB: Android Debug Bridge } This step doesn't require "Root" permission, but before proceeding into the main tutorial. We should prepare several things: Computer / Laptop running Windows OS A cable data Download ADB depedencies: here Android device with "USB debugging". If your device "cant be recognized" or simply not exist on "Device Manager", you need to install: Universal ADB Driver Then read: XDA: Install ADB & Enable USB Debugging. Now put this command on your command prompt / powershell / gitbash / or whatever terminal you use: # Check if our device works properly adb devices # Install Game Guardian manually through ADB adb install --bypass-low-target-sdk-block <path_to_game-guardian.apk> # If ADB is unresponsive / bugged, do: adb kill-server adb start-server { Termux: Terminal } The only requirement is you need "Root" permission, this is the most easiest way. Since you're going to Install Game Guardian, I assume you already have one (Yes, Game Guardian requires "Root" permission, duh). Download: Termux and Just go ahead execute this command: pkg update pkg upgrade pkg install tsu pkg install android-tools sudo adb install --bypass-low-target-sdk-block <path_to_game-guardian.apk> { Virtual Machine } This is suitable way for non-rooted users. Android 14 is relatively new, some of your ROM/OS might not support "Rooting" yet. Virtual Machine allows you to emulate another Android inside your Android 14 (or etc). Usually it comes with older Android version. I suggest to use Virtual Machine with Android 7 or 9 as you're not going to face any redundant issues, like Android 10-14 did. I would recommend using "VPhoneGaGa": VPhoneGaGa VMos Pro X8Sandbox F1VM { Modded APK } You can try to edit Game Guardian SDK: ("android:targetSdkVersion" to version 24+) and ("android:minSdkVersion" to 24+) on Manifest.xml using: APK Editor. You can also download already modded Game Guardian here (credit to @HEROGAMEOfficial ) : : Game Guardian : [ Aftermath ] With that, you can simply reference this topic in case there's someone that facing the same problem. I hope this topic can help you and other people. Thank you for reading.4 points
-
4 points
-
My grandfather used to say: "Everything is new, this is long forgotten old."4 points
-
4 points
-
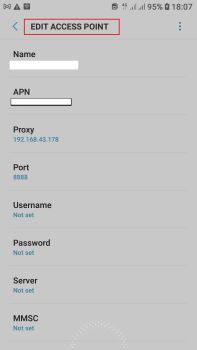
Disclaimer: This guide is for educational purposes only. The techniques explored here are intended for understanding the technical aspects of Android games. Users are advised to use this knowledge responsibly and within legal and ethical boundaries. I disclaim any liability for misuse or unauthorized activities. Use this information at your own risk. As you explore with me, remember it's all about learning, not mischief. If you decide to try out any of these tricks, make sure it's within the rules and plays nice with the devs. I'm not taking responsibility for any shenanigans, so be cool, and enjoy the learning ride. Cheers! Goals : • Identify server-side data from local data. • How to tamper server-side data . • bypass SSL encryption. Requirement : • You should be familiar with requests ( http ) . • You should have some level of knowledge about reverse-engeneering / Exploits / etc. Tools : • GameGuardian. • Frida. • IDA (Pro). • BurbSuite / any other proxy interceptor. • LUA Decryption and Encryption for cocos2dlua. Difficulty : 8/10 ----- Let's Dive IN -----First step is to collect information about the game start playing the game normally to get some information about it, it's concept and what data they have like items , coins , gems , vip , battlepass, etc and what they call it in game. Open GameGuardian or root explorer to know what engine the game use and it's libs, like libIl2cpp.so for Unity , Cocos2d for coco's 2d games , or a custom lib built on top of other games engines like libLotaApp. BurbSuite Start Intercepting traffic. Set Up Your Environment Install Burp Suite: Download and install Burp Suite from the official website. Configure Your Android Device: Connect your Android device to the same network as your computer. Go to Wi-Fi settings, find your connected network, and set the proxy to your computer's IP address and the port Burp Suite is running on (default is 8080). Step 2: Configure Burp Suite Start Burp Suite: Open Burp Suite and go to the "Proxy" tab. Configure Proxy Settings: Under the "Options" tab, go to "Proxy" settings. Ensure the proxy listener is running on the IP address and port you specified in your Android device's Wi-Fi settings. Install Burp's CA Certificate: In Burp Suite, go to "Proxy" > "Options" > "Import / export CA certificate." Click "Save CA Certificate" to save the certificate. Transfer the certificate to your Android device and install it. when Exporting the Certificate You should put the Extention of it .ctr Step 3: Configure Android Device Install and Configure Proxy on Android: Ensure the proxy listener is running on the IP address and port you specified in your Android device's Wi-Fi settings. For APN edit the Access point name : Install the Exported Certificate from burb to your Android phone Step 4: Start Capturing Traffic In the "Target" tab, you should see the target host(s) that your Android device has communicated with. Browse on Android Device: Open the browser on your Android device and start browsing. Burp Suite will capture the traffic, In the "Target" tab, you should see the target host(s) that your Android device has communicated with. Inspect and Manipulate Traffic: In the "Proxy" tab, you can intercept requests and responses, inspect them, and even manipulate them before forwarding. Use Other Burp Suite Tools: Explore other tools in Burp Suite, such as "Repeater" and "Intruder," to perform further analysis and testing. Hierarchy: The Site Map is organized in a hierarchical structure that represents the different hosts and paths your client has communicated with. Hosts and Paths: Hosts represent the web servers or domains that your client has interacted with. Paths represent specific URLs or routes within those hosts. HTTP Methods: Each entry in the Site Map includes information about the HTTP methods used (GET, POST, etc.). Status Codes: The status codes of the responses (e.g., 200 OK, 404 Not Found) are displayed, providing insights into the server's responses. Request and Response Details: Clicking on an entry in the Site Map reveals detailed information about the request and response for that specific interaction. This includes headers, parameters, and content. Filtering and Searching: You can filter and search for specific requests or hosts, making it easier to focus on relevant parts of the traffic. Context Menu: Right-clicking on an entry provides a context menu with various options, such as sending the request to other Burp Suite tools for further analysis. Interactivity: The Site Map is an interactive tool that allows you to manipulate and analyze the captured traffic in real-time. Use Cases: Analysis and Debugging: Identify patterns and anomalies in your web traffic for analysis and debugging purposes. Security Testing: Spot potential security issues, such as vulnerabilities or unusual behaviors. Mapping Application Flow: Understand how different paths in your application are accessed and interacted with. select all URLs and right click -> delete selected items ( we don't need them ) launch the app and watch what the app send when it execute I launched "Mythic Su*moner" and this traffic get captured But Most games use SSL pinning and they don't show the full trafic even when intercepting with them . in this case we need Frida to UnSSL it. ( u can use it to bypass root detection aswell ). SSL pinning, also known as certificate pinning or public key pinning, is a security mechanism employed in applications to enhance the security of SSL/TLS connections. It involves associating a specific SSL certificate or public key with a particular domain, and the application will only accept connections with that specific certificate or key. Normal SSL/TLS Connection: In a standard SSL/TLS connection, a client (e.g., a mobile app) connects to a server, and the server presents its digital certificate to the client during the handshake process. SSL Pinning Process: With SSL pinning, the client embeds a specific SSL certificate or public key within the application. When establishing a connection to the server, the client checks whether the server's presented certificate matches the embedded certificate or public key. Verification and Trust: If the presented certificate matches the pinned certificate or key, the connection is considered trusted, and the communication proceeds. If there's a mismatch or the server presents a different certificate, the connection is rejected, preventing potential man-in-the-middle attacks. Using Brbsuite To listen to the game traffic is man-in-the-middle attack. that's why Most of the trafic is rejected in the 1st capture FRIDA Connect your phone with ur pc via USB & and inject an Agent into the process to UNSSL Pinning : when You UNSSL the game you get More Trafic : With this traffic UNSSLed you can play with it, inspect it and modify it with the repeater ( this is how you hack the server-side ) this method called Tampering data. How to Identify Server Data and Local Data. Select the inapps.appflyer.com and watch it when you play every changement in data ( server side ) get registered by this url ( most cases ) it will send a gzip to server and save it there . any local data will be saved in your machine ( android device ) or memory and the inapps.appflyer.com won't send a request. Some games use SOCKET to connect the game and the server and keeps the connection open until the game get terminated or the server get shut down, with burb you can Intercept sockets aswell. TIP : while you intercepting traffic from burb open the lib with IDA pro to dissassemble it. IDA make sure IDA fully dissassemble the lib by showing idle on the buttom go to the functions menu hit ctrl + F to start searching for keywords I mentioned at the beginning ( gold , items name , coins , player stats etc ) when I search for the keywords no functions / methods found that mean the logic and the data proccess isn't in the lib nor in the traffic ( most of them ) that means the only way to store the logic is in the files in this example game. if you found functions your starting point start with frida, you can use Frida to hook it and track the pointers and afterword GG to create a script. Decrypt LUAC take the apk and unzip it ( open with rar / 7zip ) you'll end up with the game files and Done the logic is found in the game files , the game use lua to run with C and cocos2d. but the game won't leave the game logic and codes open and public the must use some sort of encryption to it , for that they use LUAC is the Lua compiler responsible for taking Lua source code and transforming it into Lua bytecode encrypted. try another file : notice : i0lzCcmB1Cjxk6DpvlmdPINybrXXeBA1 each file have this signature at the start ofthe it IDA & LUA Decryption and Encryption for cocos2dlua. copy the signature and search ida for it but this time in the string if found you should find the key aswell : I use IDA & LUA Decryption and Encryption for cocos2dlua to decrypt the files. after it's done every file will be unencrypted and easy to read : and with that data you can create anything you want / mod / script etc Why not just frida? to use frida you need a pc ( termux users isn't included because you just need a pc to use frida -_-) agents ( frida scripts ) isn't portable you always need your pc to use the script powerd with usb I mean too much pain that's why in my opinion GameGuardian is the best choice you can run the script anywhere anytime + lua much easier than js. not all libs work with libc and not all of them contain usefull resources like the example above. ---- tips : the data should be stored in -server -local machine ( your device ) the game files "apk" ( your device aswell ) look at these 3 places to find the game resource. game logic either in the files or in the lib ( like il2cpp ) android games can't afford Hosted Hypervisor for the logic processing. I can update this topic, comment out what you want to know more about ( exluding server-side hacks ) I won't provide tools all you need is your brain to outsmart devs.4 points
-
4 points
-
4 points
-
4 points
-
4 points
-
New version 11.5.1.5.1.x64 released! I added 'Search mode' for users that have problems running this script. This release also replace 'old cars unlocker' and 'single car unlocker' scripts.4 points
-
stumble this on localization.lua lmao, say alot about their care to players that gives feedbacks i also working on promocode hacks, but this one is Paid, because i need to pay the host for hosting it, alternatively you can use the script, i'll update it to 3.1, with fixes, so until it done, stay tune4 points
-
@NoFear I managed to find the ID's for the dice, which are 739FF0E960, 7551EB71F4 and 7551EEB114. After this 1.0.4. update it's not possible anymore to 'know' the dice by going offline in parallel system and do the same on the 'main' account. There is some kind of randomizer now. When going offline it's also not possible for me to alter the dice count. Maybe you can have another look how to alter the dice count, because I think all players are mainly looking for that feature. They don't really care (I think) about the rest of the game, the highest amount of dice will give you respect and jaw-breaking from your friends and family4 points
-
https://www.mediafire.com/file/mepx82j23mrw33c/rr3_car_upgrader.v11.4.1.4.9.x64.bin.lua/file4 points
-
4 points
-
X32 True : ~A MOV R0, #0x1 ~A BX LR False : ~A MOV R0, #0x0 ~A BX LR Int : -------------------------------- -- 9999 ~A MOVW R0, #0x270F ~A BX LR -------------------------------- -- 99999999 ~A MOVW R0, #0xE0FF ~A MOVT R0, #0x05F5 ~A BX LR Float : --100 ~A MOVT R0, #0x42C8 ~A VMOV S15, R0 ~A VMOV.F32 S0, S15 ~A BX LR ------------------- --50 ~A MOVT R0, #0x4248 ~A VMOV S15, R0 ~A VMOV.F32 S0, S15 ~A BX LR ------------------- --10 ~A MOVT R0, #0x4120 ~A VMOV S15, R0 ~A VMOV.F32 S0, S15 ~A BX LR ------------------- --0.1 ~A MOVW R0, #0xCCCD ~A MOVT R0, #0x3DCC ~A VMOV S15, R0 ~A VMOV.F32 S0, S15 ~A BX LR ------------------- --0.01 ~A MOVW R0, #0xD70A ~A MOVT R0, #0x3C23 ~A VMOV S15, R0 ~A VMOV.F32 S0, S15 ~A BX LR ------------------- --999999999.999999999 ~A MOVW R0, #0x6B28 ~A MOVT R0, #0x4E6E ~A VMOV S15, R0 ~A VMOV.F32 S0, S15 ~A BX LR Double : --100 ~A MOV R0, #0x0 ~A MOVT R1, #0x4059 ~A VMOV D16, R1, R0 ~A VMOV.F64 D0, D16 ~A BX LR ------------------- --50 ~A MOV R0, #0x0 ~A MOVT R1, #0x4049 ~A VMOV D16, R1, R0 ~A VMOV.F64 D0, D16 ~A BX LR ------------------- --10 ~A MOV R0, #0x0 ~A MOVT R1, #0x4024 ~A VMOV D16, R1, R0 ~A VMOV.F64 D0, D16 ~A BX LR ------------------- --0.1 ~A MOVW R0, #0x999A ~A MOVT R0, #0x9999 ~A MOVW R1, #0x9999 ~A MOVT R1, #0x3FB9 ~A VMOV D16, R1, R0 ~A VMOV.F64 D0, D16 ~A BX LR ------------------- --0.01 ~A MOVW R0, #0x999A ~A MOVT R0, #0x9999 ~A MOVW R1, #0x9999 ~A MOVT R1, #0x3FB9 ~A VMOV D16, R1, R0 ~A VMOV.F64 D0, D16 ~A BX LR ------------------- --999999999.999999999 ~A MOV R0, #0x0 ~A MOVW R1, #0xCD65 ~A MOVT R1, #0x41CD ~A VMOV D16, R1, R0 ~A VMOV.F64 D0, D16 ~A BX LR X64 True : ~A8 MOV R0, #0x1 ~A8 RET False : ~A8 MOV R0, #0x0 ~A8 RET Int : -- 9999 ~A8 MOVK R0, #0x270F ~A8 RET --99999999 ~A8 MOVK W0, #0xE0FF, LSL #16 ~A8 MOVK W0, #0x05F5, LSL #32 ~A8 RET Float : --100 ~A8 MOVK W0, #0x0000, LSL #16 ~A8 MOVK W0, #0x42C8, LSL #32 ~A8 FMOV S15, W0 ~A8 VMOV.F32 S0, S15 ~A8 RET ----------------------------- --50 ~A8 MOVK W0, #0x0000, LSL #16 ~A8 MOVK W0, #0x4248, LSL #32 ~A8 FMOV S15, W0 ~A8 VMOV.F32 S0, S15 ~A8 RET ----------------------------- --10 ~A8 MOVK W0, #0x0000, LSL #16 ~A8 MOVK W0, #0x4120, LSL #32 ~A8 FMOV S15, W0 ~A8 VMOV.F32 S0, S15 ~A8 RET ----------------------------- --0.1 ~A8 MOVK W0, #0xCCCD, LSL #16 ~A8 MOVK W0, #0x3DCC, LSL #32 ~A8 FMOV S15, W0 ~A8 VMOV.F32 S0, S15 ~A8 RET ----------------------------- --0.01 ~A8 MOVK W0, #0xD70A, LSL #16 ~A8 MOVK W0, #0x3C23, LSL #32 ~A8 FMOV S15, W0 ~A8 VMOV.F32 S0, S15 ~A8 RET ----------------------------- --99999999.99999999 ~A8 MOVK W0, #0xBC20, LSL #16 ~A8 MOVK W0, #0x4CBE, LSL #32 ~A8 FMOV S15, W0 ~A8 VMOV.F32 S0, S15 ~A8 RET Double : --100 ~A8 MOVZ X0, #0x0 ~A8 MOVK X0, #0x0, LSL #16 ~A8 MOVK X0, #0x0, LSL #32 ~A8 MOVK X0, #0x4059, LSL #48 ~A8 FMOV D16, X0 ~A8 VMOV.F64 D0, D16 ~A8 RET ----------------------------- --50 ~A8 MOVZ X0, #0x0 ~A8 MOVK X0, #0x0, LSL #16 ~A8 MOVK X0, #0x0, LSL #32 ~A8 MOVK X0, #0x4049, LSL #48 ~A8 FMOV D16, X0 ~A8 VMOV.F64 D0, D16 ~A8 RET ----------------------------- --10 ~A8 MOVZ X0, #0x0 ~A8 MOVK X0, #0x0, LSL #16 ~A8 MOVK X0, #0x0, LSL #32 ~A8 MOVK X0, #0x4024, LSL #48 ~A8 FMOV D16, X0 ~A8 VMOV.F64 D0, D16 ~A8 RET ----------------------------- --0.1 ~A8 MOVZ X0, #0x999A ~A8 MOVK X0, #0x9999, LSL #16 ~A8 MOVK X0, #0x9999, LSL #32 ~A8 MOVK X0, #0x3FB9, LSL #48 ~A8 FMOV D16, X0 ~A8 VMOV.F64 D0, D16 ~A8 RET ----------------------------- --0.01 ~A8 MOVZ X0, #0x147B ~A8 MOVK X0, #0x47AE, LSL #16 ~A8 MOVK X0, #0x7AE1, LSL #32 ~A8 MOVK X0, #0x3F84, LSL #48 ~A8 FMOV D16, X0 ~A8 VMOV.F64 D0, D16 ~A8 RET ----------------------------- --99999999.99999999 ~A8 MOVZ X0, #0xFFFF ~A8 MOVK X0, #0xFFFF, LSL #16 ~A8 MOVK X0, #0xD783, LSL #32 ~A8 MOVK X0, #0x4197, LSL #48 ~A8 FMOV D16, X0 ~A8 VMOV.F64 D0, D16 ~A8 RET • You can find lua code to convert any value to ARM -> HERE ----> If you get an error comment it out4 points
-
4 points
-
3 points
-
3 points
-
64bit game pointer search use Qword. 32bit game pointer search use Dword. Which are you? if next to the game process name on the top left corner near the game logo had [x64] then its 64bit game. if none then its 32bit game and use Dword.3 points
-
3 points
-
New version 11.5.1.3.1.x64 released! Added 'search mode' for more compatibility Removed car reset functionality3 points
-
This post cannot be displayed because it is in a forum which requires at least 1 post to view.
-
if people that knowns somethings about something shares, it's like opening a pandora box at first i thought i can just EOL revolted on v3 and move on, but after watching a series of video by some internet security and such, the dude name in youtube was LiveOverflow, i thought myself, what if i can tamper the connection, so i tried to bruteforce the encryption first, but then i realize this is not a normal data transfer, so i look up the source and as expected it's encrypted, and since then ive been snooping the request and such, but like always, just if the community just like Unknowncheats, this game will be dead eons ago. anyway, i found a modifier that modify the search quantity accidentally when i trying to find alternative for leveling let's say you search a pharmacy, you'll get 1-4 amount of certain meds, and since i found this modifier, you know can get 10K+ i also found alot of multiplayer settings, unprotected, just as it, Gift Limit, Chat cooldown, banned items, opening gift cooldown, i kinda want to scrap the idea to try replay attacks on websocket connection. cuz like i dont find anything special from it, i'll try to unban myself without slash command by mod, if i do, i wouldnt be surprised i think i should make YT tutorials for day r hacking lmao imma start with caps, cuz all i see on yt is "this hacks doesn't work after 766, devs patched it"3 points
-
imma chill now, i've been trial and error for 6 hours, and yeah, cool innit, free hacks for yall and me dying kek3 points
-
3 points
-
Hi @DARK_DEMON_SCRIPTER, can you tell me: what's the problem that forbids you from accessing the site? So here's some alternative: 1) You can use: Aurora Store. It is an alternative to Google Playstore with much ability such as: Multi-thread downloads, Able to download Older version of the game based on Version Codes, allows you to spoof Architecture (you can choose any architecture you want) 2) You can use: Raccoon. It is for PC though (Linux, MacOS, Windows). You can download any APK from Google Playstore through that (not 3rd-party server). So it is a good alternative. 3) If your Internet Provider forbids you from accessing the site, you can use Custom DNS: 1.1.1.1 (CloudFlare) or 94.140.14.140 (AdGuard). Or you can use VPN in general. Feel free to ask me, if you curious about VPN or Custom DNS. Please provide more context regarding your problem. If possible; attach some screenshot, so I can understand more about the problem.3 points
-
I have been lurking as a Guest on this thread, but I have signed up here to respond to your findings - This is absolute garbage of a game, and it is highly addicting if you have a group of friends that made it a bit competitive. Anyway, the trick you found is helpful, and thank you for sharing it with us.3 points
-
This post cannot be displayed because it is in a forum which requires at least 1 post to view.



.thumb.jpg.2985ee18f499743e5bfceb4f03deca48.jpg)